Investigating a Web brute force attack on Splunk
In this writeup we will be investigating a Web brute force attack on Splunk 🎯
Challenge Scenario
 |
|---|
| CTF Challenge |
We can extract some the key information from the challenge description:
- The target server has the IP address 192.168.250.70 which means it’s the destination IP address
- We need to investigate in HTTP traffic since it is a web brute force attack as mentioned
Find Attacker’s IP Address
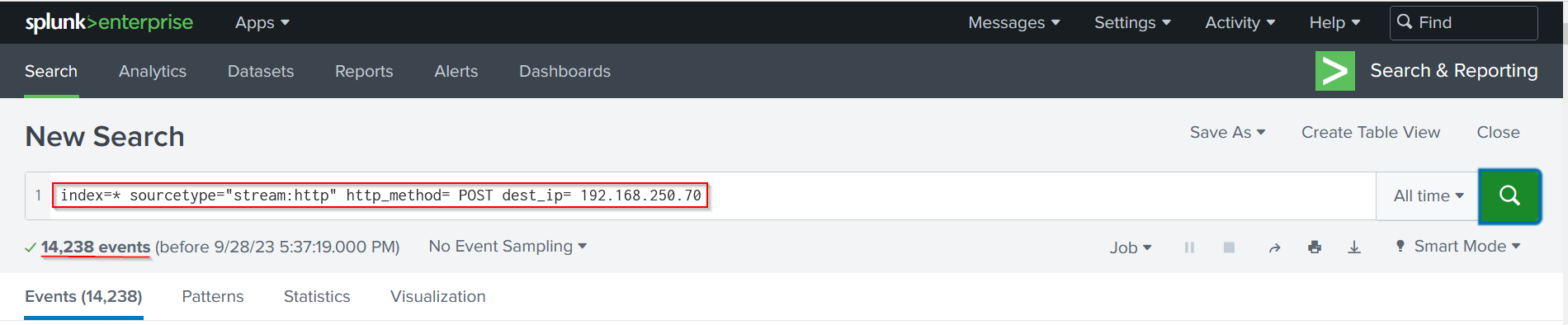
We will use the following splunk query to figure out the attacker:
 |
|---|
| Splunk Query |
explanation:
sourcetype = "stream:http": since the attack is a web brute forcehttp_method = POST: because brute force attacks are performed through login forms to authenticate users and the HTTP method most often used for authentication is the “POST” method.dest_ip=192.168.250.70: becasue the target server is at 192.168.250.70, so all the HTTP traffic will be coming to this address.
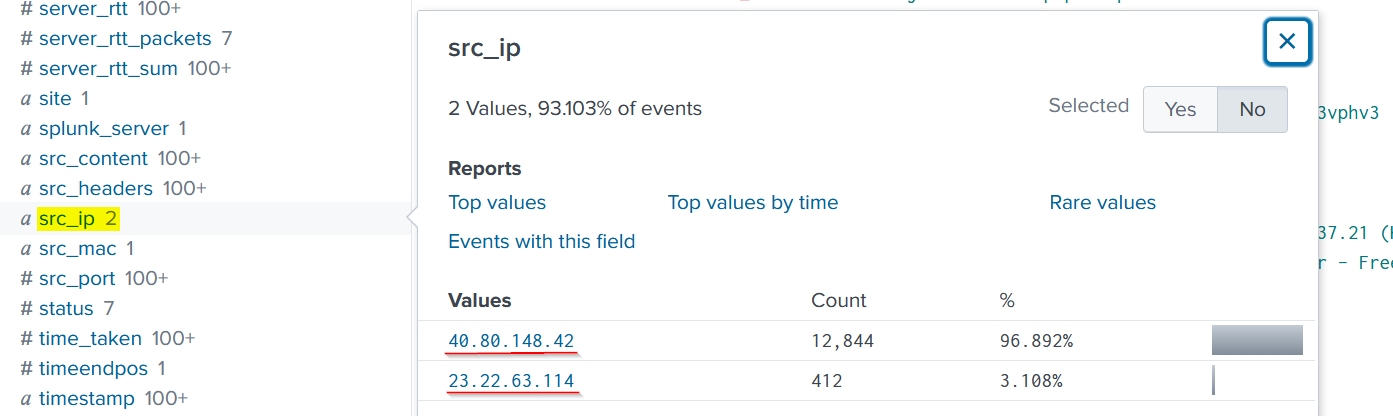
let’s see the source IPs we have in the src_ip field from the search result:
 |
|---|
| Source Addresses |
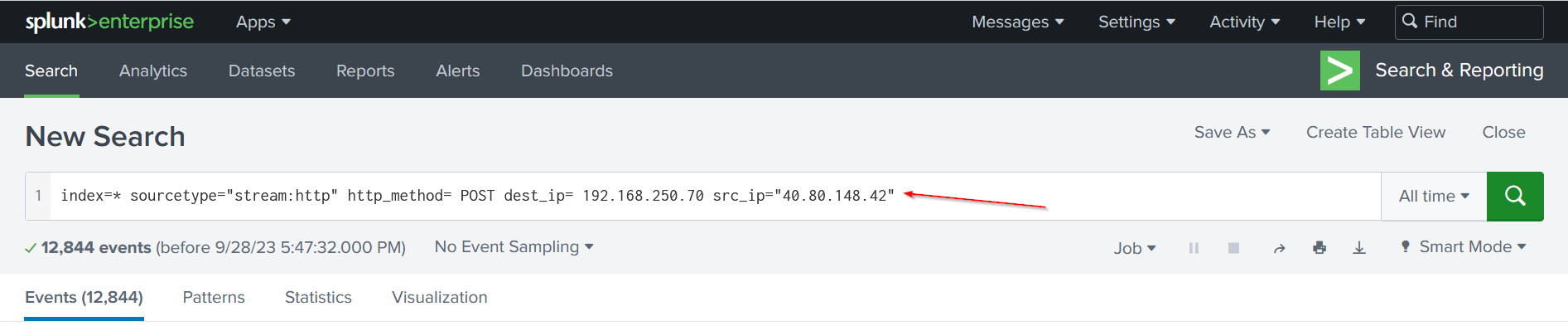
We have 2 source IP addresses. We will add the first one which is 40.80.148.42 to the previous search query to see the traffic originating from this address:
 |
|---|
| Search Query |
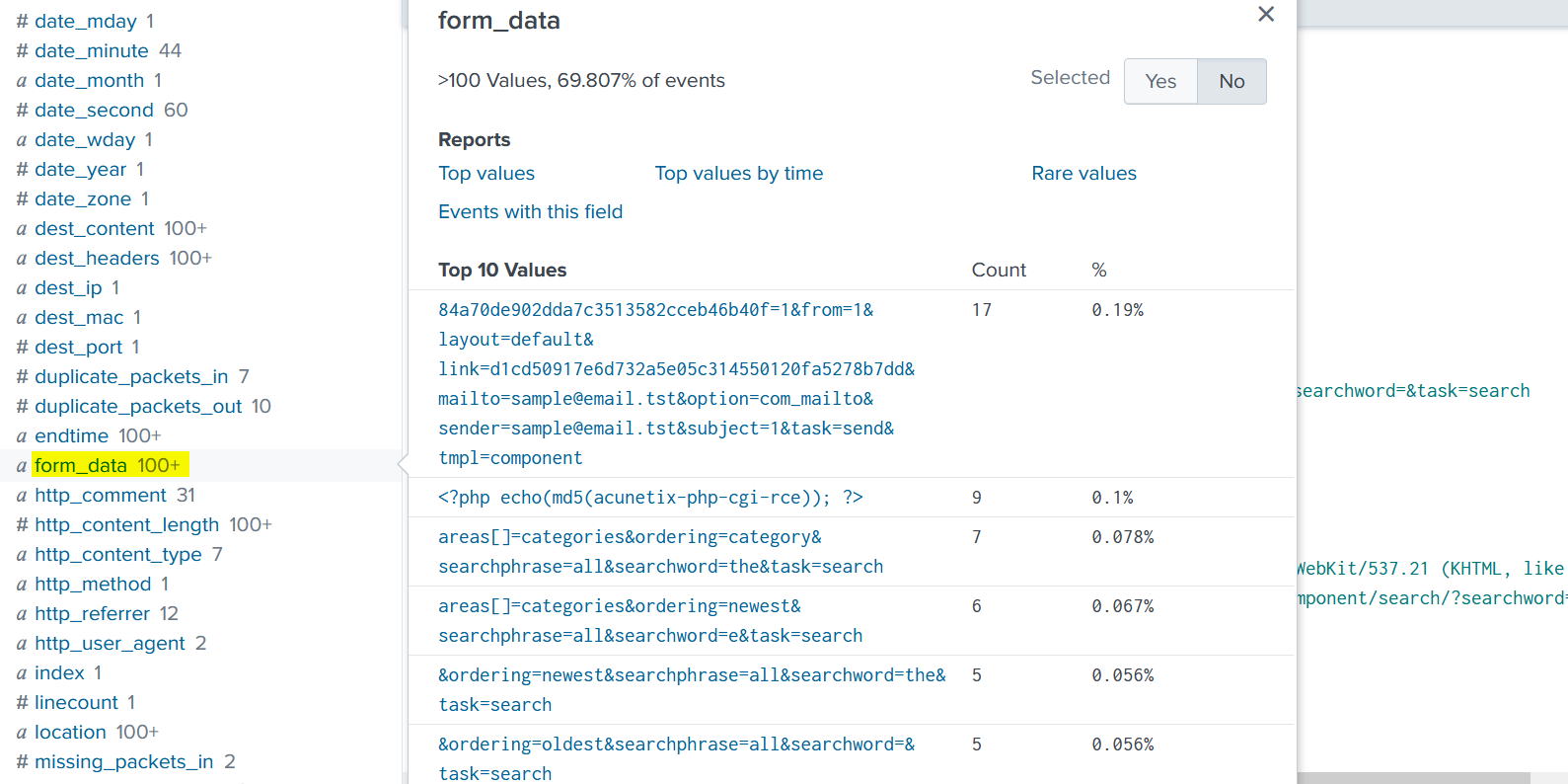
To see the traffic content related to “POST” requests we have to check the form_data field:
 |
|---|
| Form Data Of 40.80.148.42 IP Address |
The content is clean and nothing indicates that there was a brute force attack.
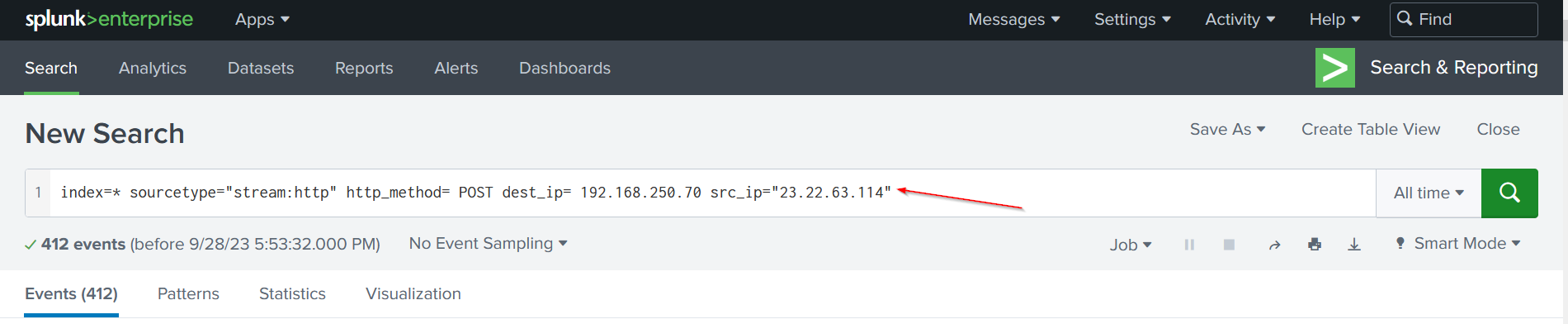
Let’s move to the second source IP address which is 23.22.63.114:
 |
|---|
| Search Query |
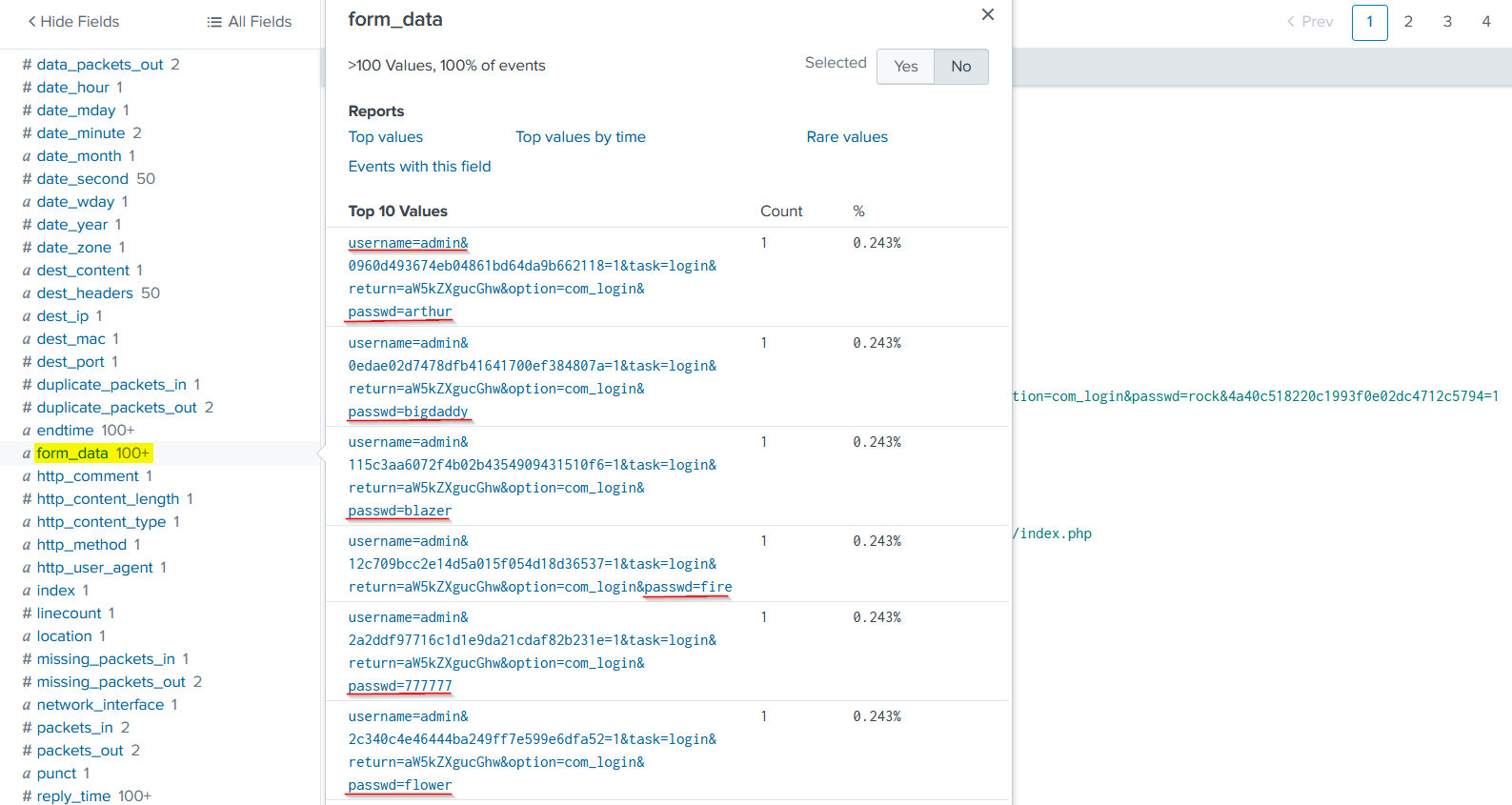
We found 412 events related to this query. Next, We will check the form_data field to see the HTTP traffic originating from this address:
 |
|---|
| Form Data Of 23.22.63.114 IP Address |
It’s obviously a brute force attack as we notice many login attempts with username “admin” and multiple passwords. The attacker tried to get the administrator account !
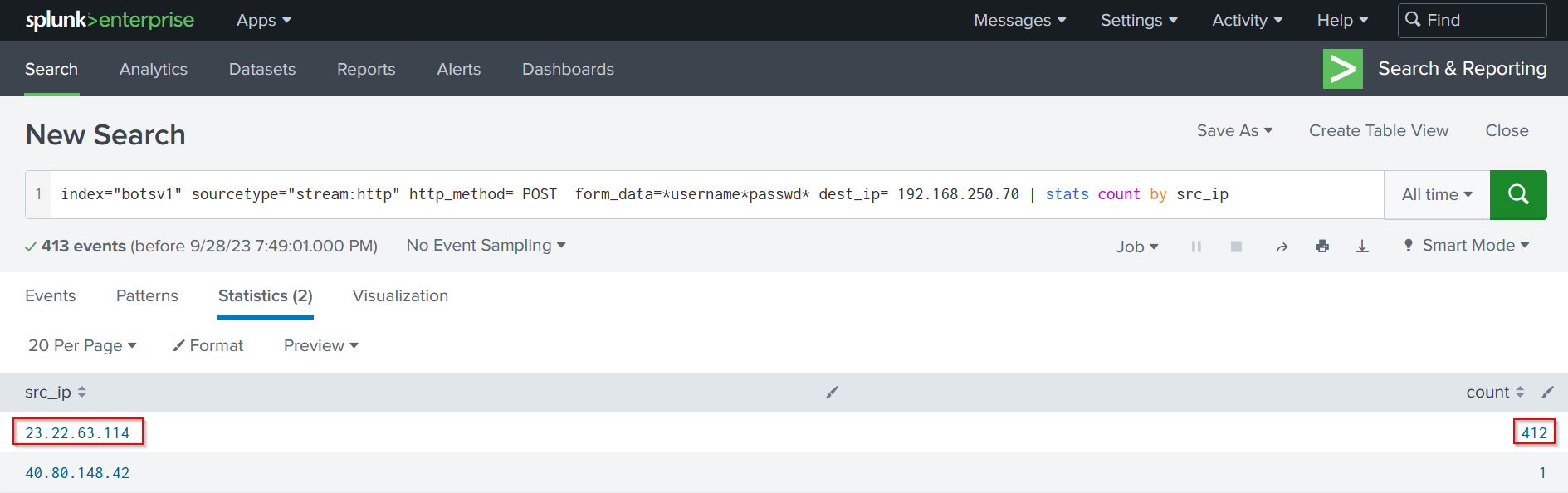
Before moving to next step, we have to confirm what we found by counting the number of attaker’s IP address to see how many login attempts were made:
 |
|---|
| Counting Login attempts |
The count of the 23.22.63.114 attacker IP address is way higher than the other source IP address.
We can conclude that a brute force attack was performed on the web server by the 23.22.63.114
Find The Password Length
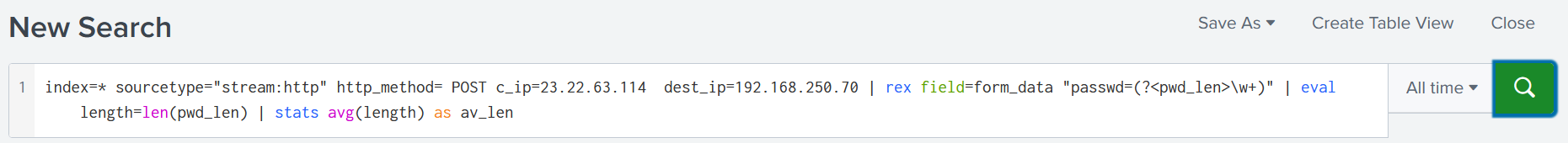 |
|---|
| Search Query For Password Length |
In the previous search we used rex command to extract password length using regular expressions at search time by:
- specifying
form_dataas field to rex from - specifying “passwd=(?
\w+)" as regular expression
💡
? : match zero or one
w+ : means “one or more alphanumeric characters.”
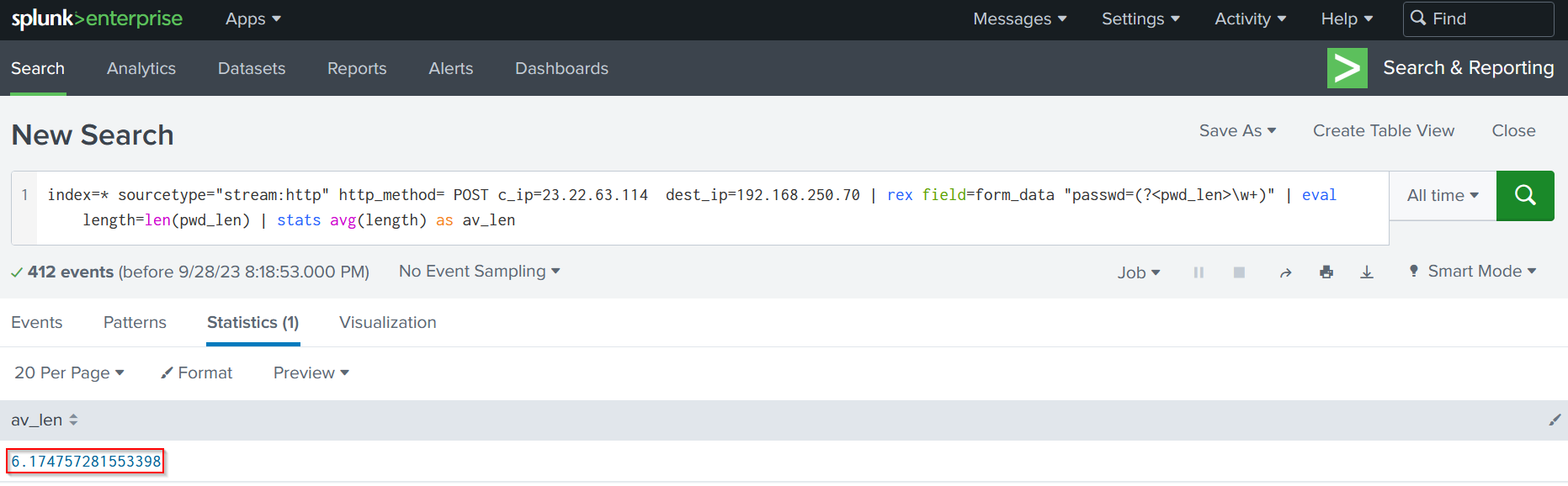 |
|---|
| Result |
As shown in the previous screenshot, The password length is 6 since the result is 6.1774…
🚩Flag:
flag{23.22.63.114_6}
![]()
“To beat a hacker, you have to think like a hacker” 💙



