Follina zero-day vulnerability exploited after malicious file execution
Today we will be investigating The SOC173 Case on LetsDefend plateform.
Let’s start 🎯
Security Alert
Alert
 |
|---|
| incident details |
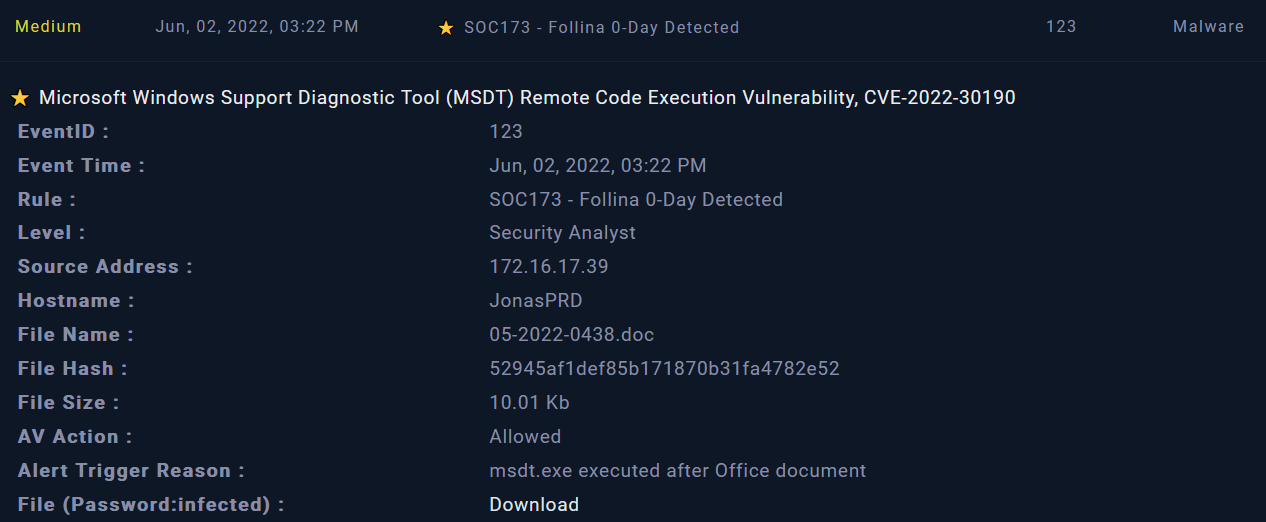
The alert provides us with many key information as a start point of our investigation such as :
- Source address: 172.16.17.39
- Hostname: JonasPRD
- File name and File Hash
From the reason of triggering the alert we can understand that a file called msdt.exe was executed on JonasPRD machine.
What is Follina Vulnerability
Before we proceed to detection and analysis phase we should understand the Follina vulnerability and how it works so we can easily investigate the incident.
📍 Follina is a remote code execution vulnerability (RCE) discovered in the Microsoft Office suite of products. This vulnerability can be exploited when MSDT (Microsoft’s Support Diagnostic Tool) is called using the URL protocol from an application (for example: Microsoft Word). The MSDT (msdt.exe) is typically used to collect information and report system crashes to Microsoft support.
Follina vulnerability occurs when user open a Microsoft Office document such as a Word docx file containing malware delivered via email for example. That’s explains why Threat actors exploit Follina through phishing campaigns.
NIST assigned Follina the Common Vulnerabilities and Exposure (CVE) number CVE-2022-30190 for tracking purposes.
Detection and Analysis
VirusTotal & AnyRun
We will use VT and AnyRun Sandbox to analyze the suspicious file using its Hash
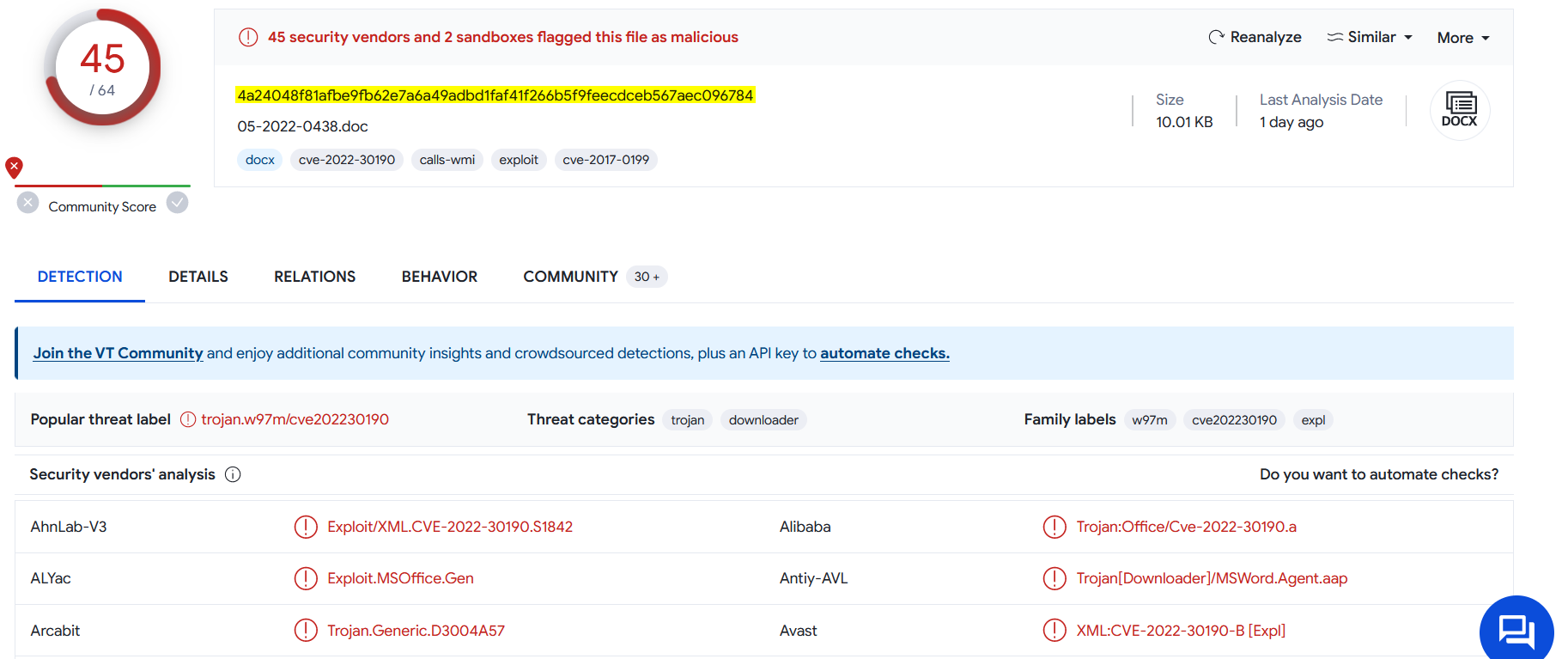
📍 Analysis with VirusTotal :
 |
|---|
| VT Analysis |
The file seems to be malicious !
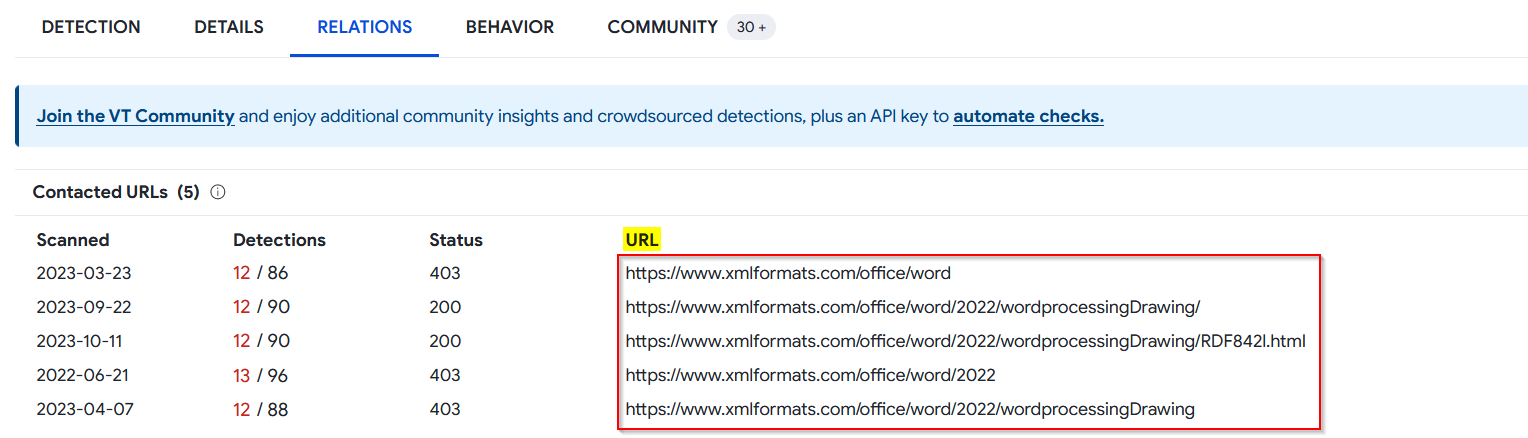
If we look at the Relations Tab we will find the contacted URLs related to this file:
 |
|---|
| Contacted URLs |
We’ll take note of these URLs as they will be needed when investigating the log management.
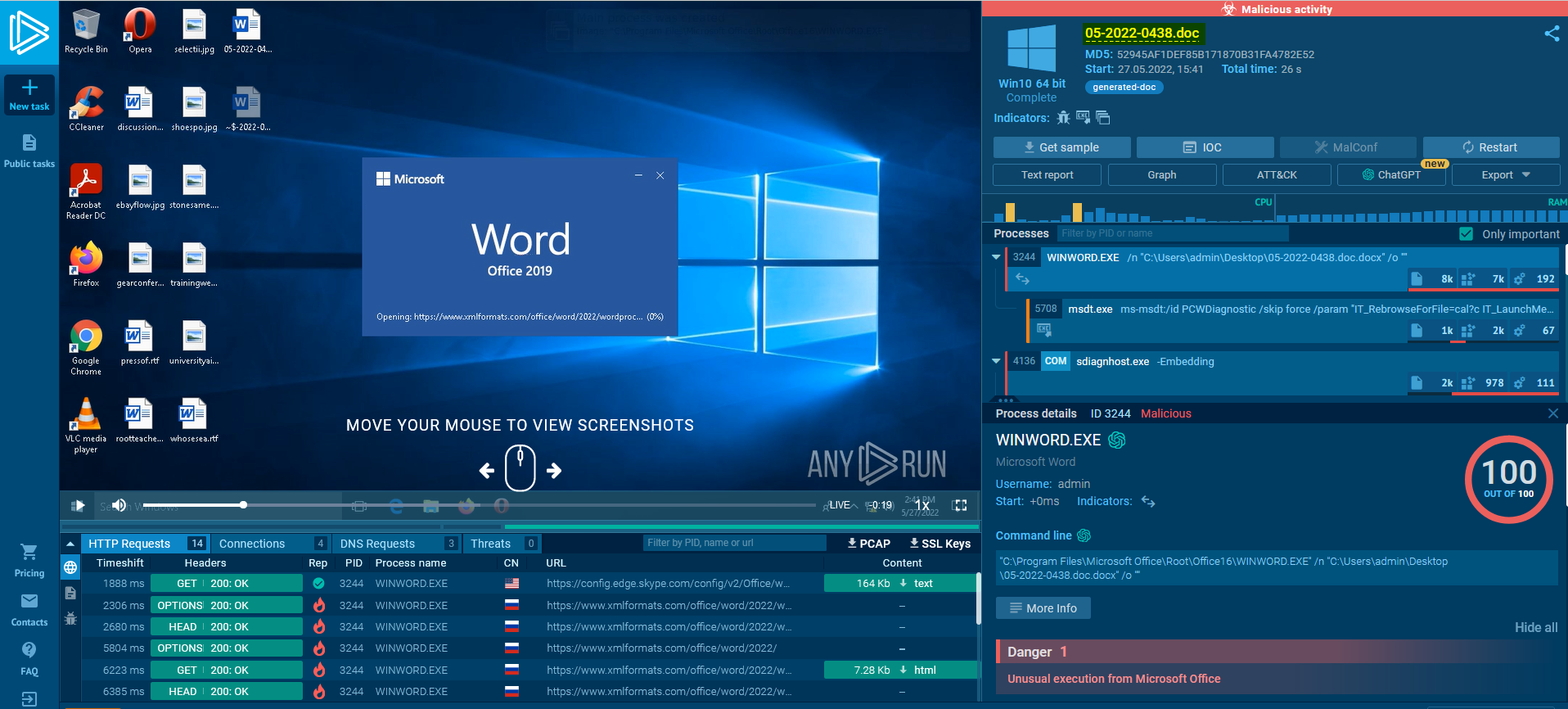
📍 Analysis with AnyRun :
It’s time to conduct a dynamic analysis to understand how the malware behaves using AnyRun:
 |
|---|
| Dynamic Analysis using AnyRun |
We can see the all malicious HTTP requests made by this malware:
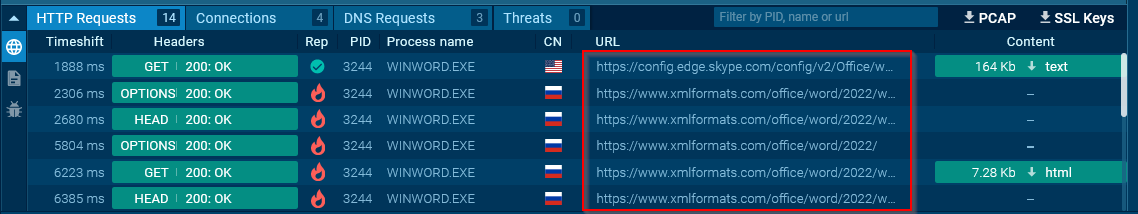 |
|---|
| Malicious HTTP requests |
And executed processes:
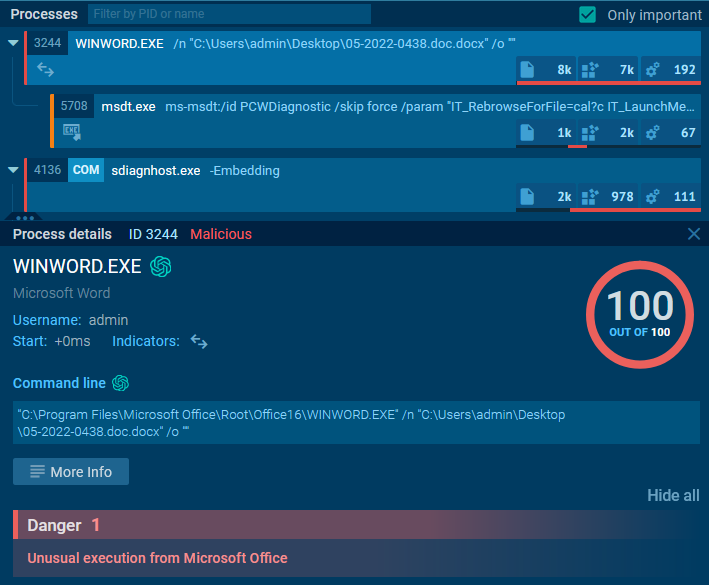 |
|---|
| Malicious Processes |
Initial Access
Before proceeding to log management and endpoint investigation we need to find how the malicious file was delivered.
As we mentioned before, Threat actors exploit Follina through phishing campaigns. If we look at the mail inbox of JonasPRD, we will find the next:
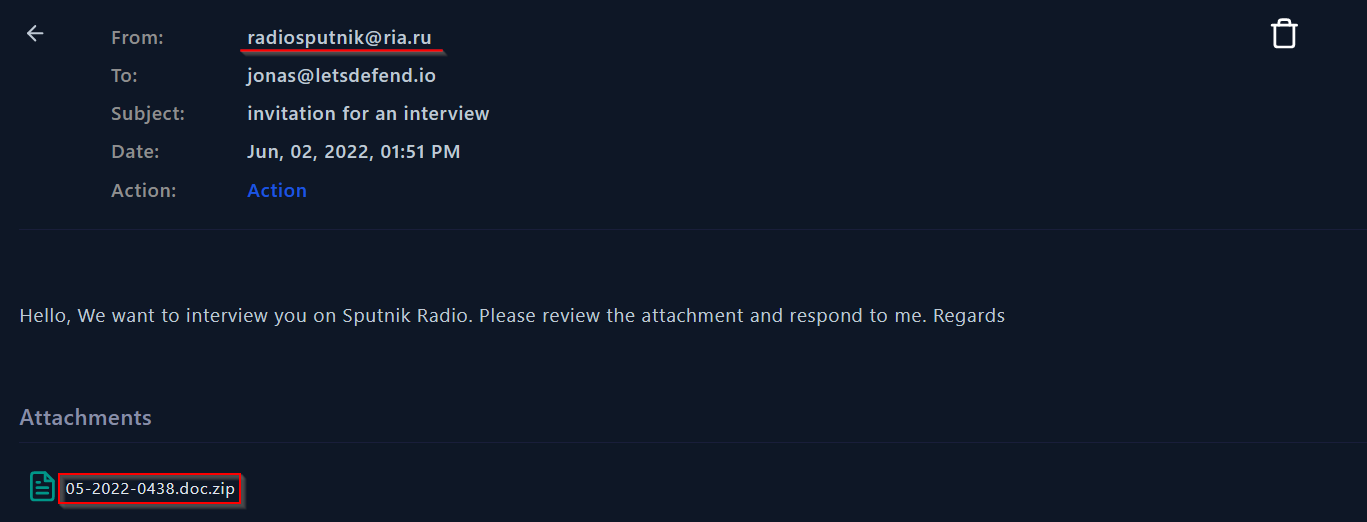 |
|---|
| Email with file attachment |
The attacker send the malicious file through a phishing email!
Log Management
It’s time to investigate the log management to see if the malicious URLs found previously in VT and AnyRun were accessed by the victim:
 |
|---|
| Search Query |
7 events are related to JonasPRD machine.
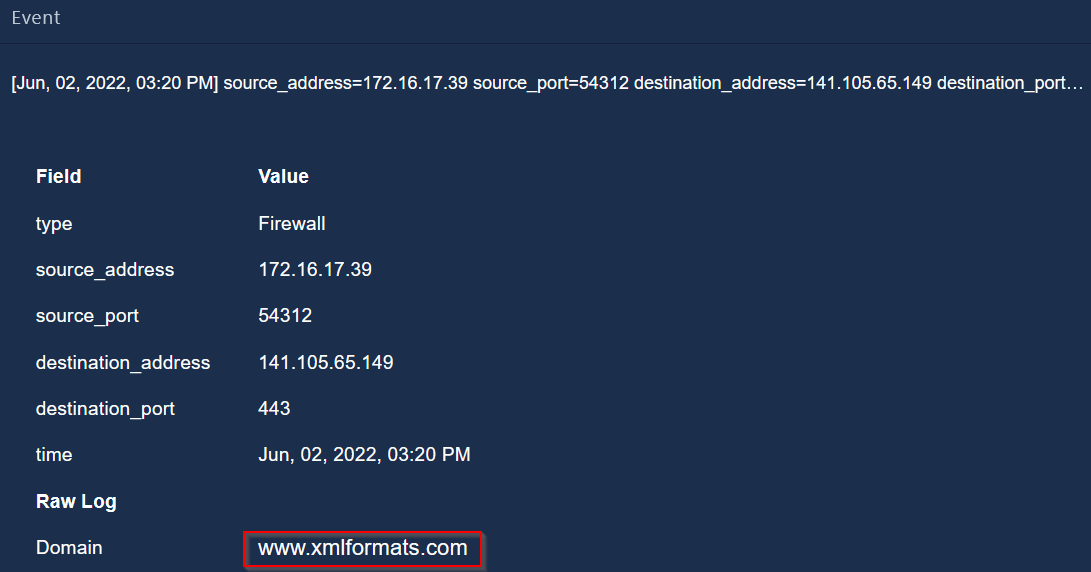 |
|---|
| C2 address is accessed by the victim |
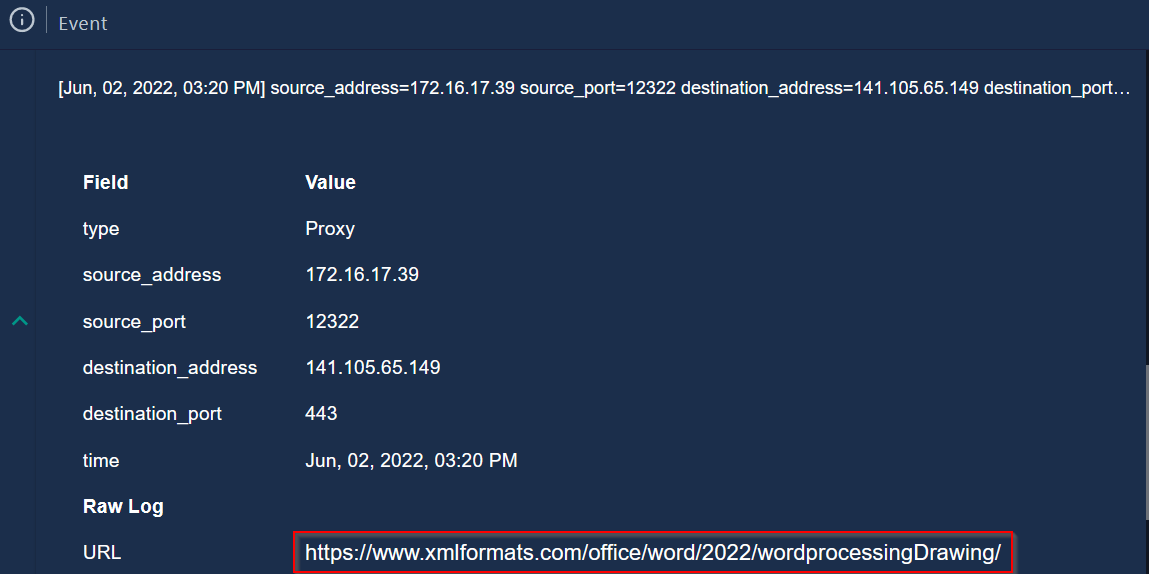 |
|---|
| C2 address is accessed by the victim |
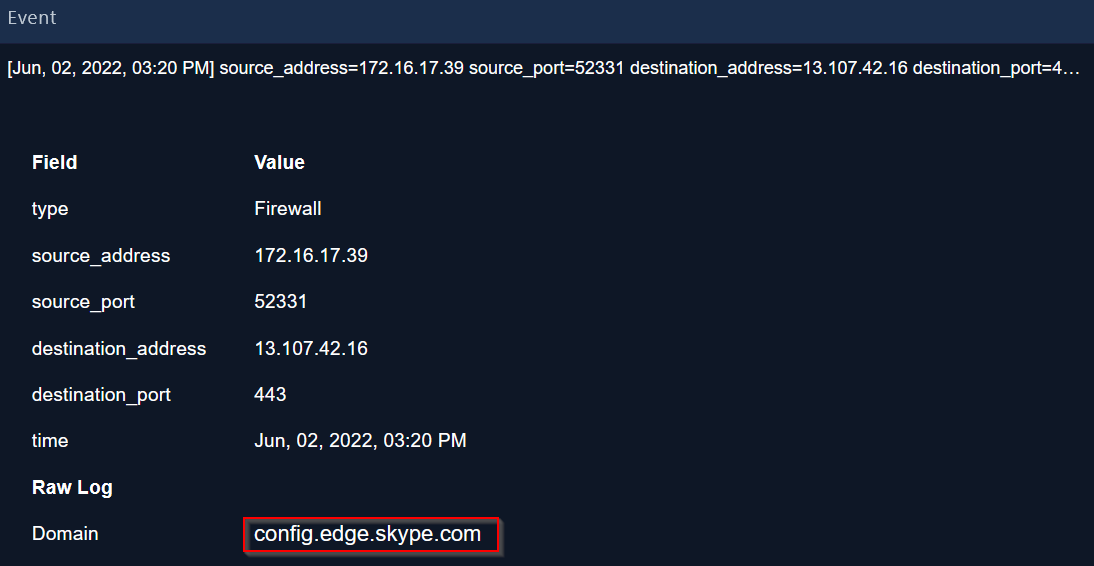 |
|---|
| C2 address is accessed by the victim |
The other 4 addresses are also malicious URLs related to the malware.
Endpoint Security
As a final step in detection and analysis phase, we will see if the malicious file was executed on the victim’s machine by looking at Processes tab in the endpoint section:
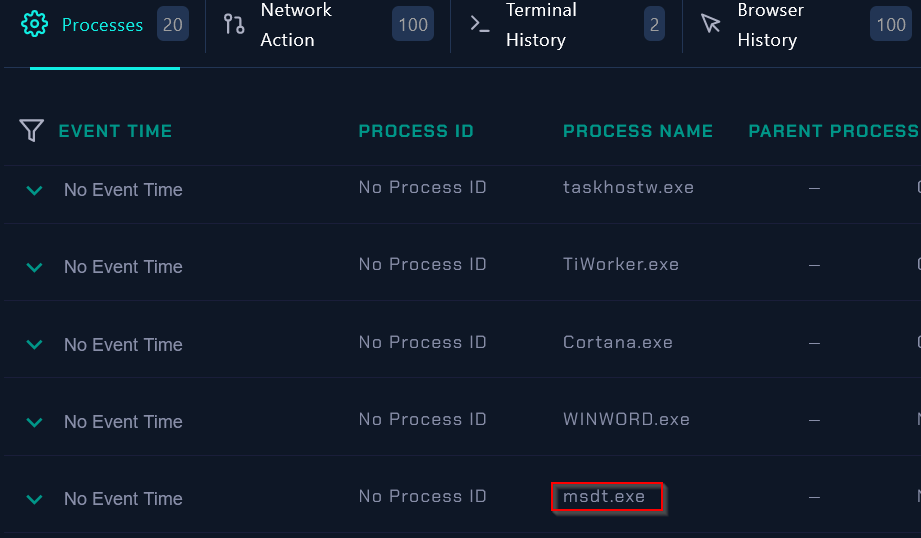 |
|---|
| Malicious Process |
We are sure the malicious process was executed hence we can confirm the attack was successful and JonasPRD machine was compromised !
Containment
As the JonasPRD device is compromised, we should contain it immediately and isolate it from the network to prevent the attacker from reaching all other devices.
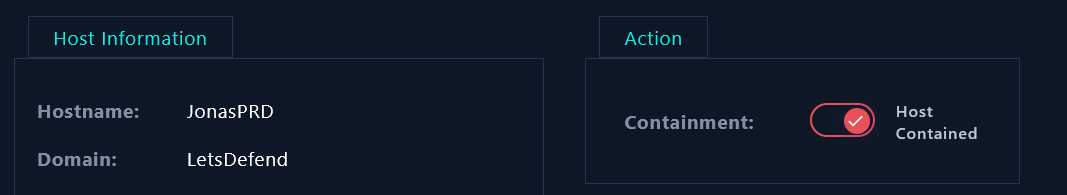 |
|---|
| Compromised machine is contained |
Artifacts
We have to collect all the data found previously during the investigation that includes malicious URLs, file hash, email address of the sender so we can add it to EDR (Endpoint Detection and Response) to avoid similar attack in the future:
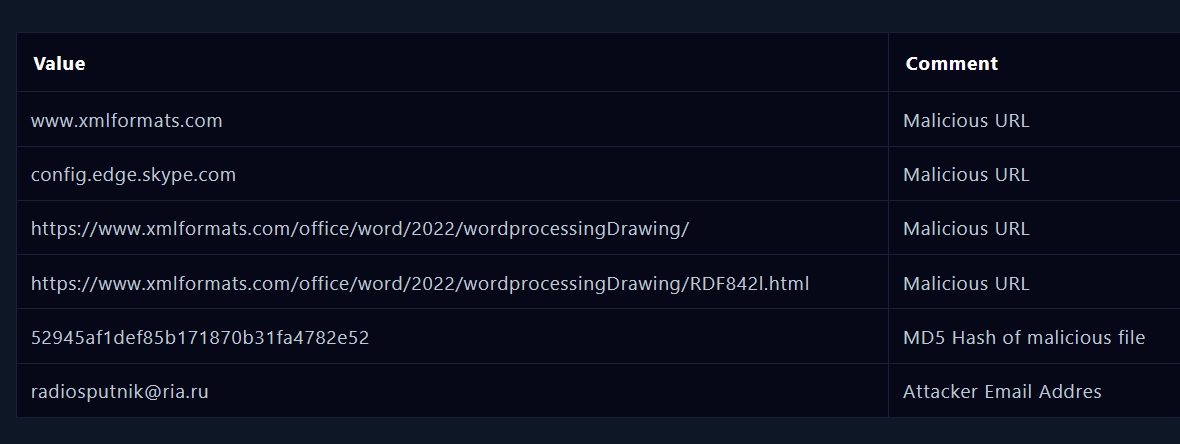 |
|---|
| Adding artifacts |
Close Alert
The incident is identified as True Positive (TP). We can close the alert !
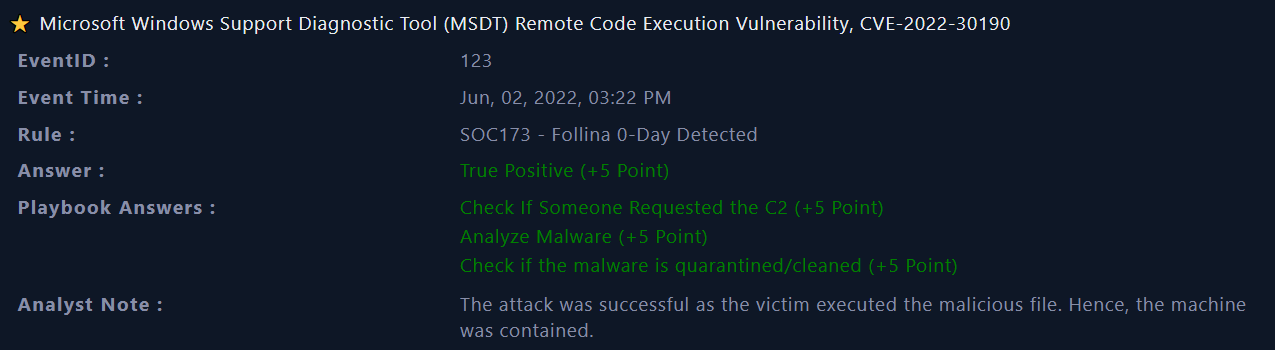 |
|---|
| Alert closed |
![]()
“To beat a hacker, you have to think like a hacker” 💙



