Investigating web attacks as a SOC Analyst - Possible LFI Attack
Today we will be investigating a security alert on LetsDefend plateform. This writeup will explain how to respond to a security alert on SOC department following the incident response steps.
Let’s start 🎯
Security Alert
Alert
The monitoring page provides us the incident details such as event ID, source and destination IP address, the URL requested and much more as shown in the screenshot below :
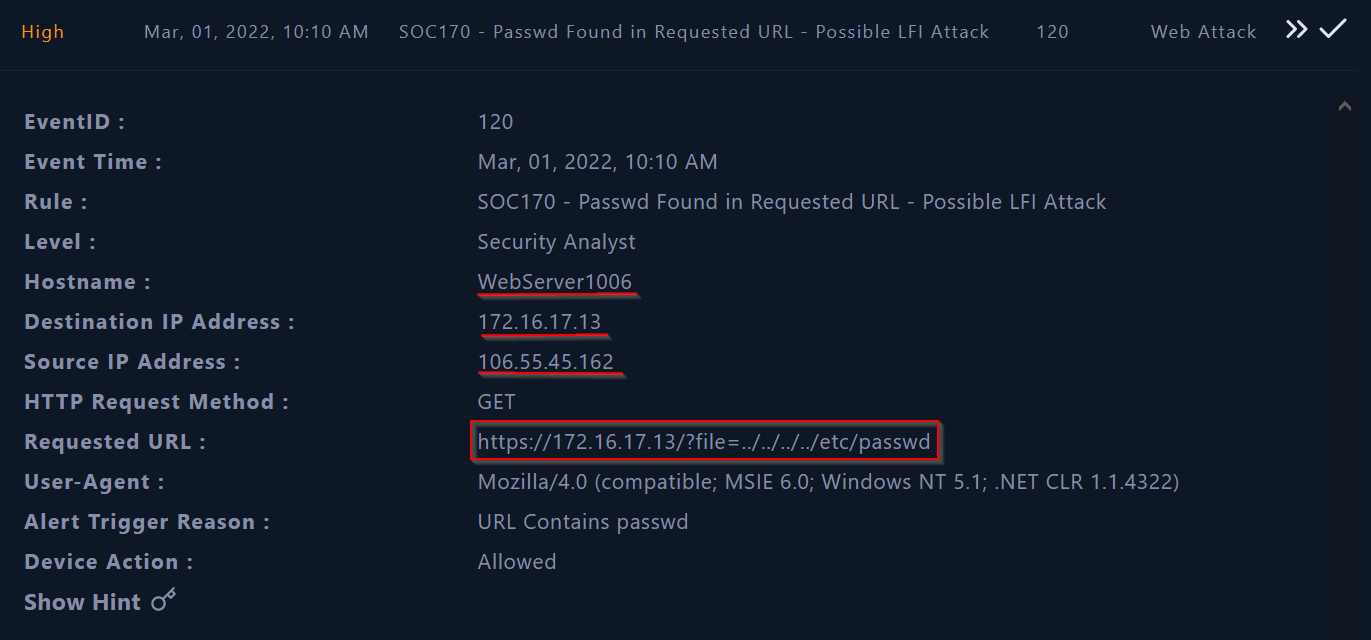 |
|---|
| incident details |
Understand Why the Alert Was Triggered
Instead of starting the analysis directly, first we have to understand why this rule was triggered by examining the rule name to understand which attack we are facing. Then we have to detect between which two devices the traffic is occurring.
From the previous picture we can understand that an attacker with IP address 106.55.45.162 tried to get the passwd file from the host 172.16.17.13.
💡 The /etc/passwd file is a plain text file with information for all user accounts. It includes a list of user accounts on the system, as well as details such as user ID, group ID, home directory, and default shell.
Let’s dive into analysis and detection phase !
Detection and Analysis
Examine Logs
I started my analysis from log management to see if there’s any logs related to attacker’s IP :
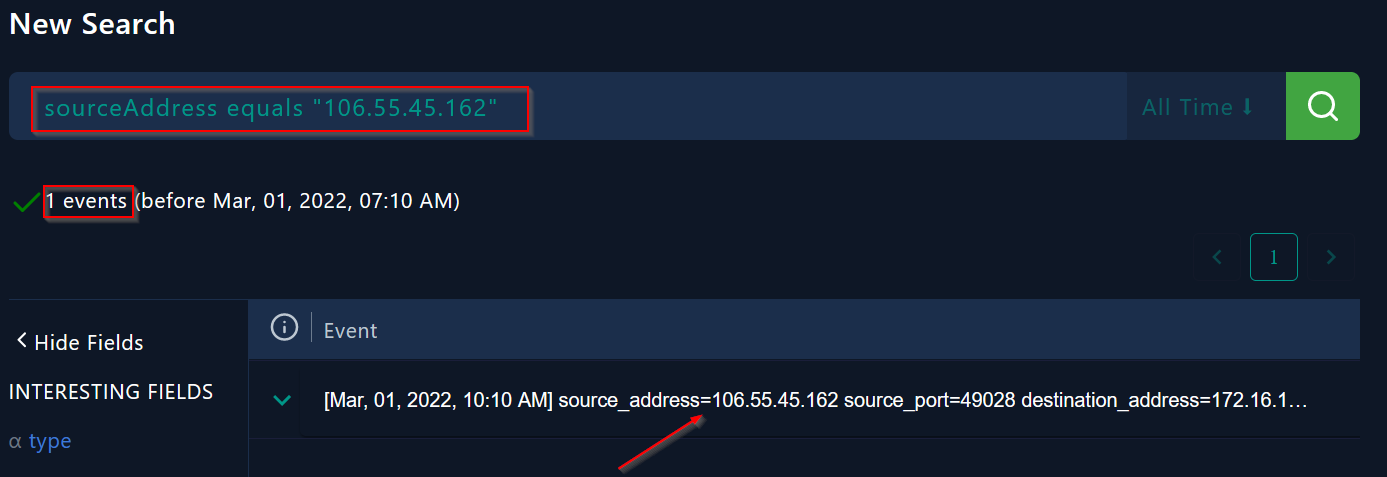 |
|---|
| Log Search Query |
There is 1 event found :
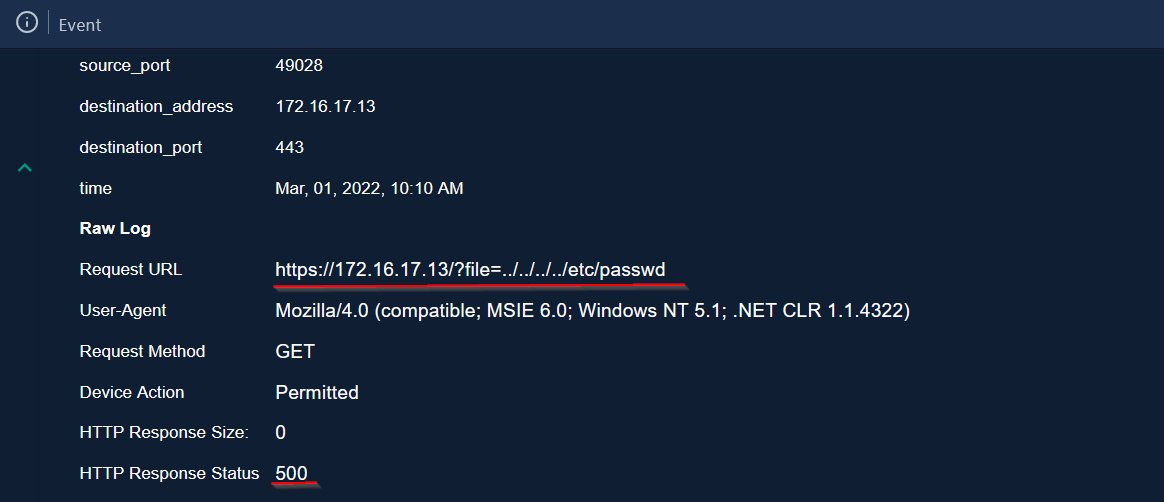 |
|---|
| Security Event |
The attacker has made a malicious request to get passwd file and the server response was 500 (Internal Server Error ), This indicates that the server encountered an unexpected condition that prevented it from fulfilling the request.
In the Endpoint security I searched for the victim IP hostname to collect more data :
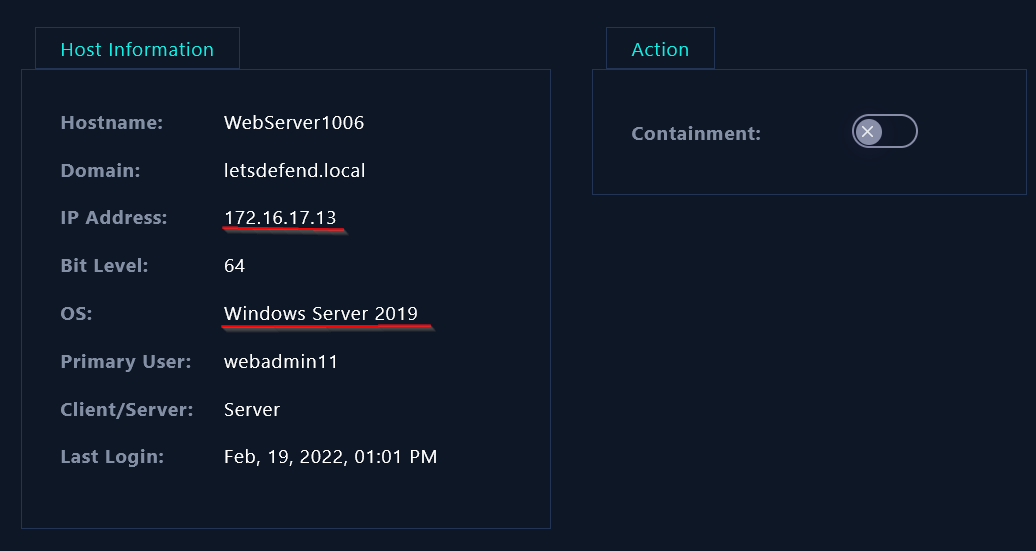 |
|---|
| Victim Host Information |
The victim host is a Windows Server 2019 which explains why the attack was not successful since there is no passwd file on Windows system.
IP Reputation
In this step I will use VirusTotal and AbuseIPDB to check the reputation of the source IP address.
📍 VirusTotal :
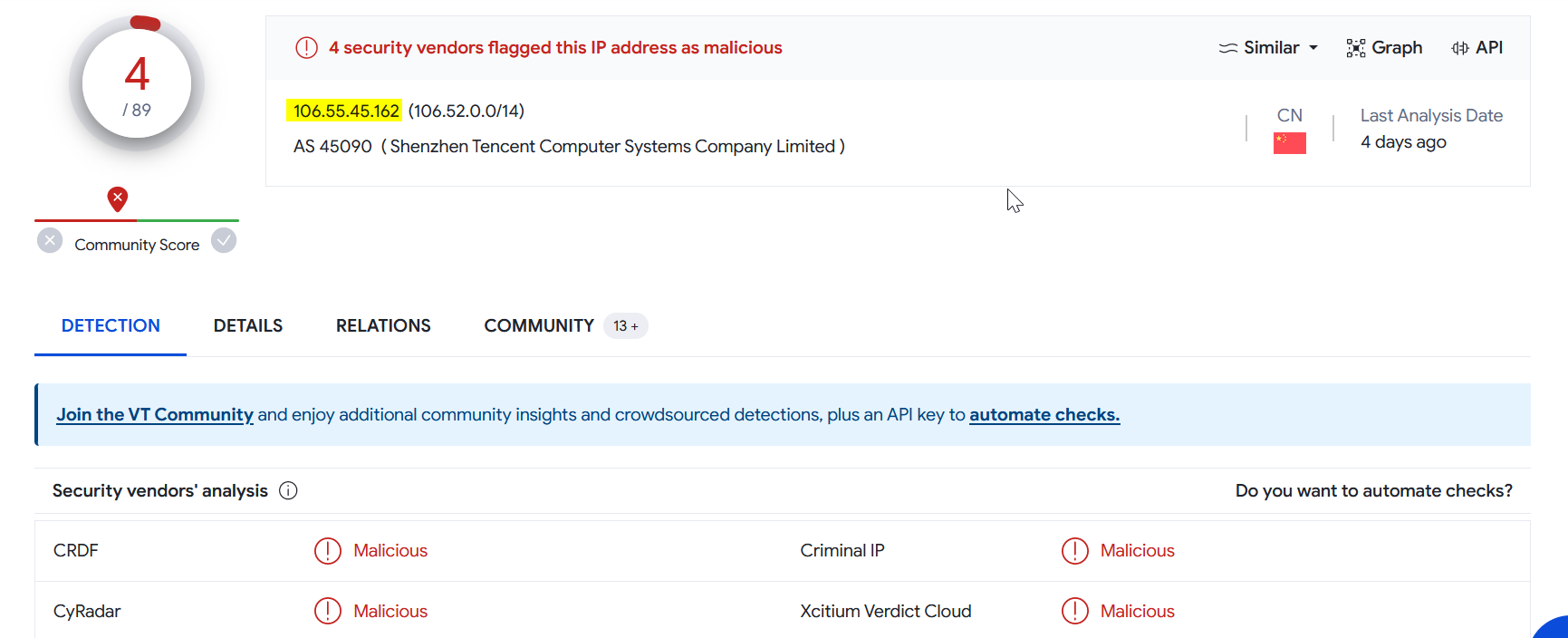 |
|---|
| IP Reputation on ViruTotal |
📍 AbuseIPDB :
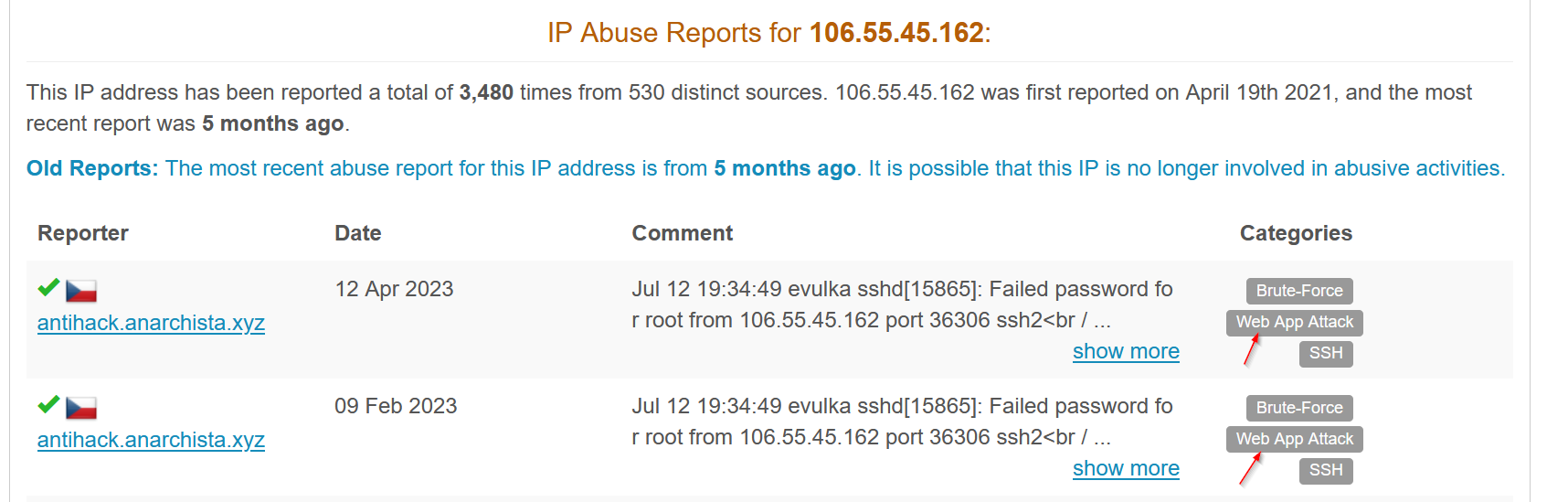 |
|---|
| IP Reputation on AbuseIPDB |
We can confirm that the source IP address is malicious and coming from outside to company network.
Do We Need Tier 2 Escalation?
Tier 2 escalation should be performed in cases where the attack succeeds and since the the status code is 500 and the response size is 0 we can confirm that the attack was unsuccessful. Thus, there is no need to contain the device or escalate the incident to the next level.
Artifacts
In this step, we will add artifacts to our EDR to avoid a similar incident in the future. Artifacts are residual traces left behind by the actions of attackers or malicious actors within a computer system or network.
I will add the malicious IP address of the attacker :
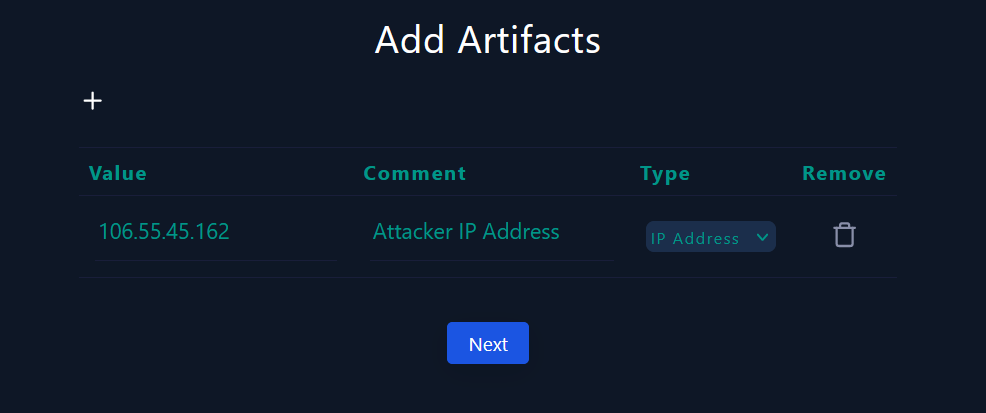 |
|---|
| Adding artifacts |
Playbook
A security playbook is a list of required steps and actions needed to successfully respond to any incident or threat.
We will answer the following questions :
- Is Traffic Malicious? Yes, Malicious
- What is the attack vector in the malicious traffic you have detected as a result of your investigations? Local File Inclusion (LFI)
- Is the malicious traffic caused by a planned test? Not Planned
- What Is the Direction of Traffic? (Format: Source -> Destination) Internet -> Company Network
- Was the Attack Successful? No
- Do You Need Tier 2 Escalation? No
Close Alert
Finally, the incident is identified as True Positive (TP) and was mitigated successfully. We can close the alert !
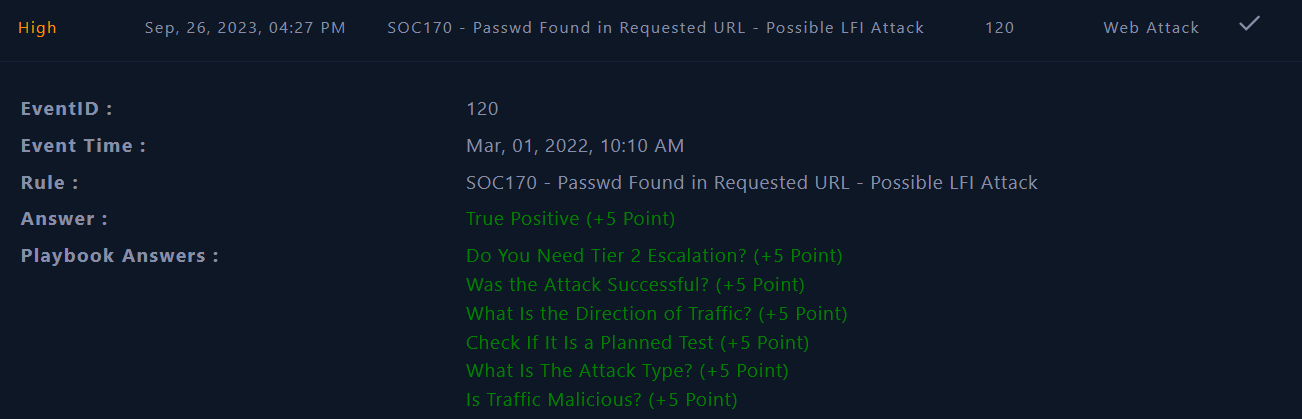 |
|---|
| Alert closed |
Challenge Report
Personal Challenge Report on LetsDefend
![]()
“To beat a hacker, you have to think like a hacker” 💙



