Analyzing XLS File
Today we will solve the “Remote Working” challenge on LetsDefend. We will work on an XLS zipped file to answer the questions and complete the challenge.
📌 File Downlaod :
NOTE : Do not open on your local environment. It is a malicious file.
First we will download the zip file and extracted in our virtual environment to keep our local machine safe.
The XLS file that should be analyzed is called “ORDER SHEET & SPEC.xlsm” as shown in the screenshot below :
 |
|---|
| The Extracted XLS File |
📌 Analysis With VirusTotal :
We uploaded the XLS File into VT and it seems to be malicious as indicated below :
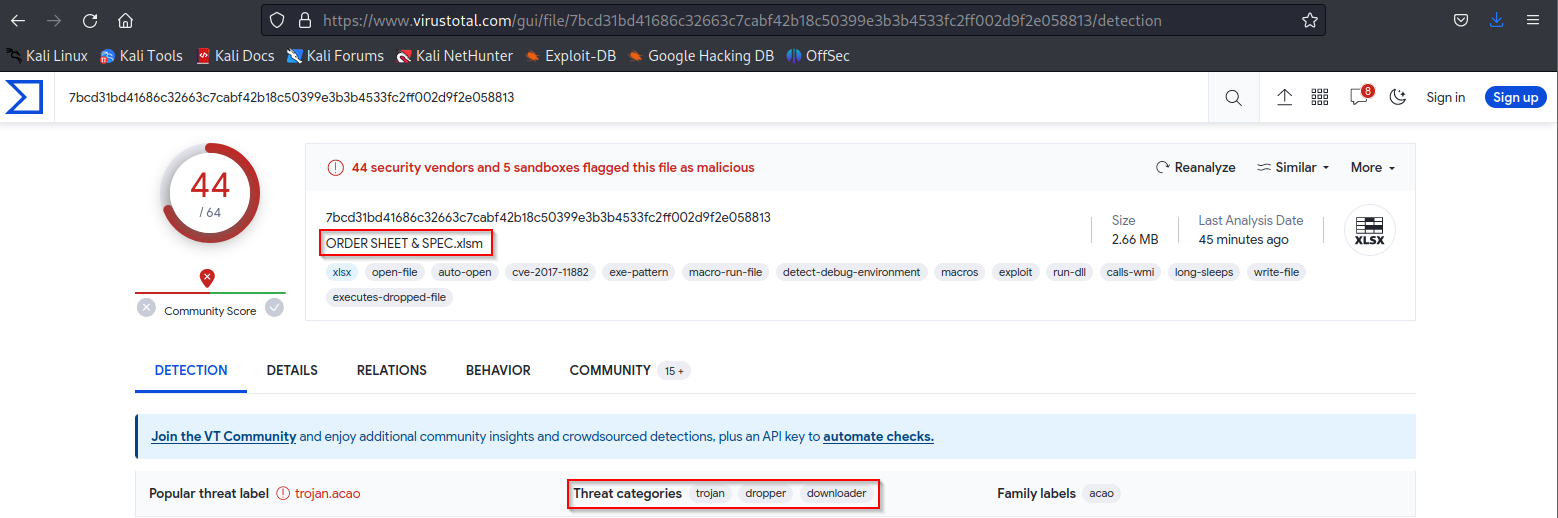 |
|---|
| File Analysis with VT |
We will examine all the information provided by VT to answer the challenge questions.
🚩 What is the date the file was created?
To answer this question, we will open up the Details tab and scroll down to History section where the creation time is indicated as below :
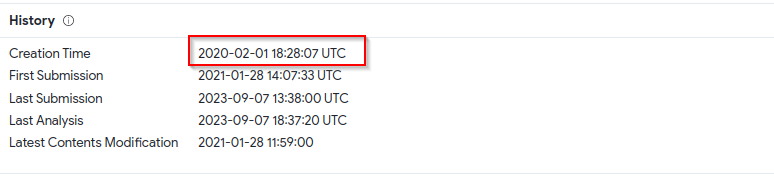 |
|---|
| File Creation Time |
 |
|---|
| Challenge Question 1 |
🚩 With what name is the file detected by Bitdefender antivirus?
back again the Detection tab, we will look in the Security Vendor’S Analysis list for BitDefender.
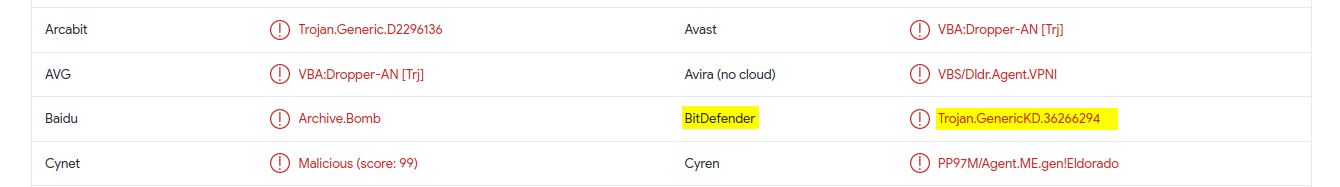 |
|---|
| Malicious File name according to BitDefender |
The malicious XLS File is detected by BitDefender as “trojan.generickd.36266294”
 |
|---|
| Challenge Question 2 |
🚩 How many files are dropped on the disk?
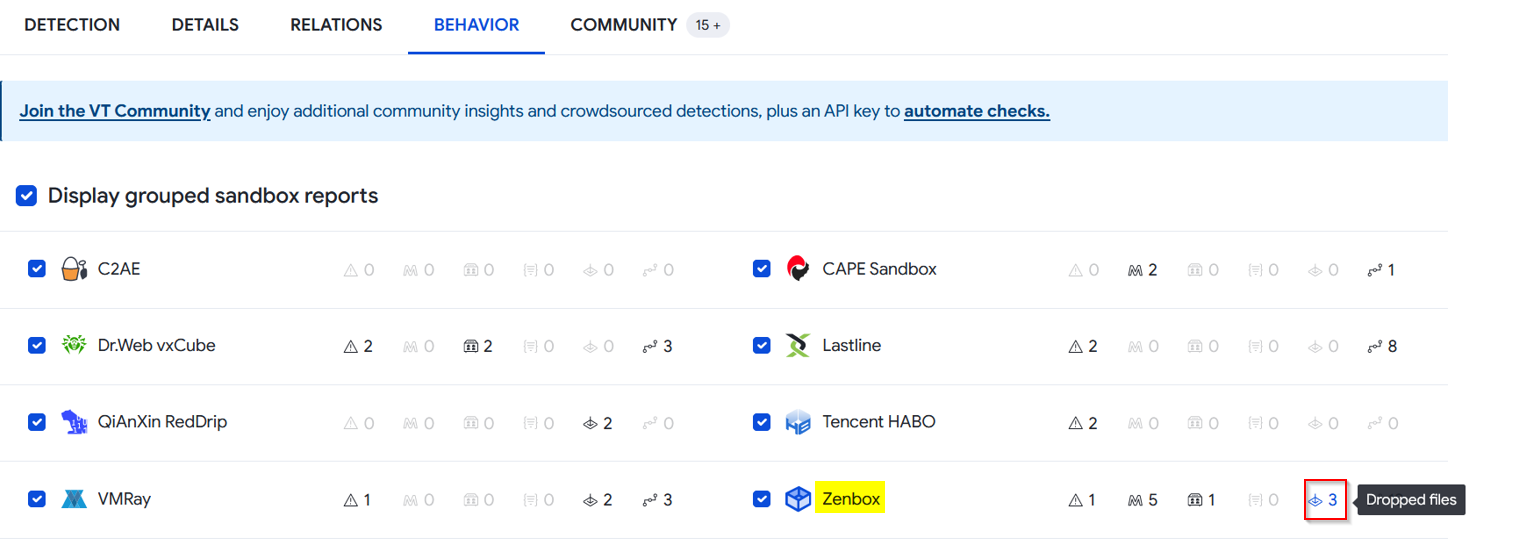
According to VirusTotal, files_dropped contains a list of all files are files specifically created and written to during an execution recording. These files are found under Behavior tab in the SandBox reports. We will go for Zenbox which indicate 3 dropped files.
 |
|---|
| Dropped Files |
We have 3 dropped files !
 |
|---|
| Challenge Question 3 |
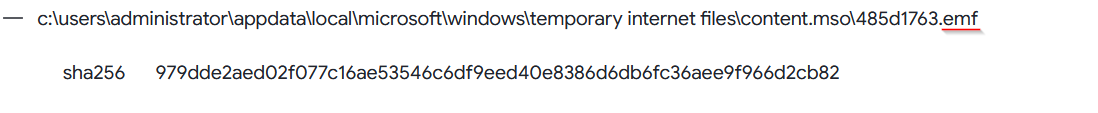
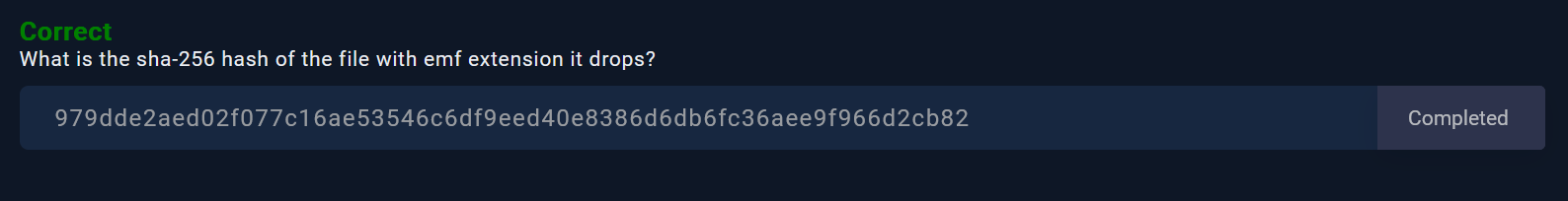
🚩 What is the sha-256 hash of the file with emf extension it drops?
Always under Behavior tab, we ca find more details about these dropped files such as full path, file name and SHA256 Hash in the Dropped Files section :
 |
|---|
| SHA256 Hash of dropped file with emf extension |
 |
|---|
| Challenge Question 4 |
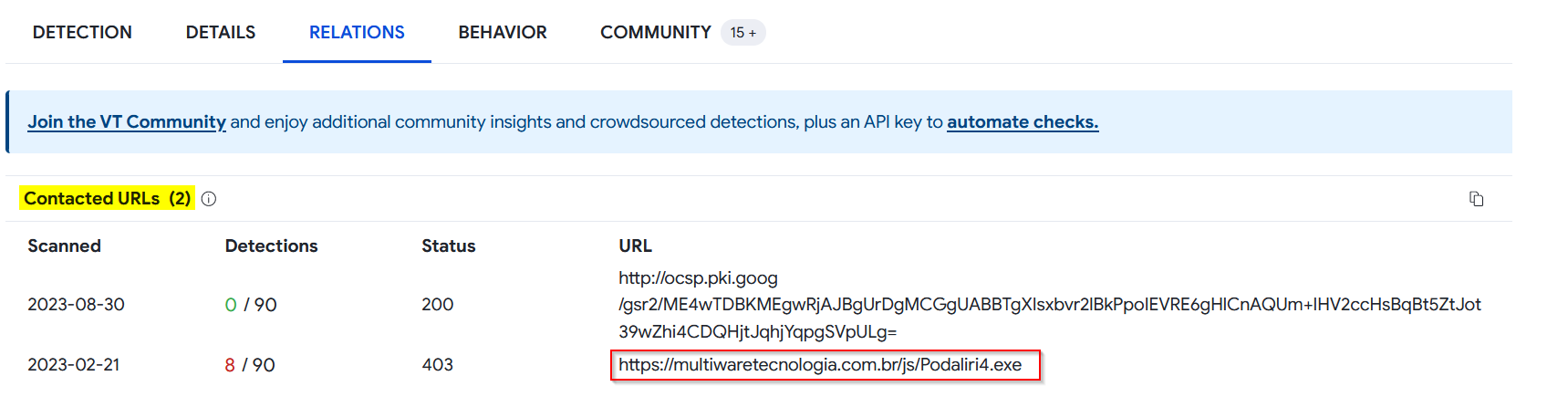
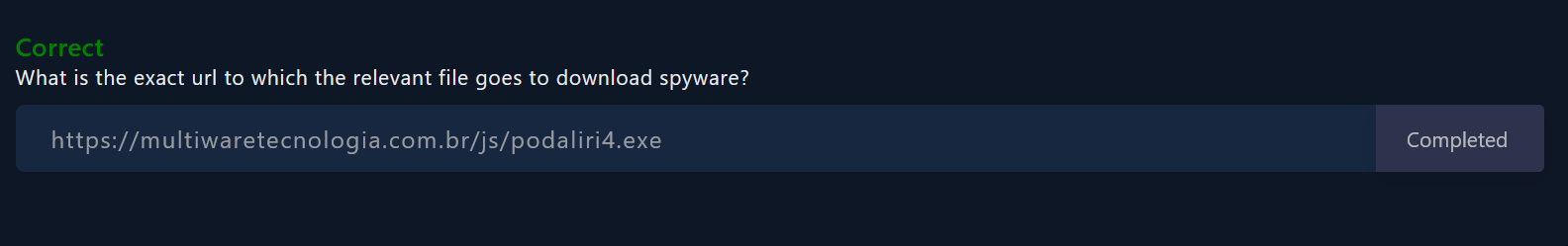
🚩 What is the exact url to which the relevant file goes to download spyware?
All URLs related to a malicious file are given under Relations tab in Contacted URLs section.
VT has identified 2 URLs :
 |
|---|
| Contacted URLs |
 |
|---|
| Challenge Question 5 |
The Remote Working Challenge is completed successfully. This Easy Level challenge allows us to use VirusTotal and analyze a malicious XLS File to find creation time, dropped files, C2 URLs and much more !
 |
|---|
| Challenge Badge |
![]()
“To beat a hacker, you have to think like a hacker” 💙