Investigating the famous malware Emotet detected in a word ducument on LetsDefend
Today we will be investigating The SOC109 Case on LetsDefend plateform. In this case, the Emotet malware will be discussed and analyzed in details.
Let’s start 🎯
Security Alert
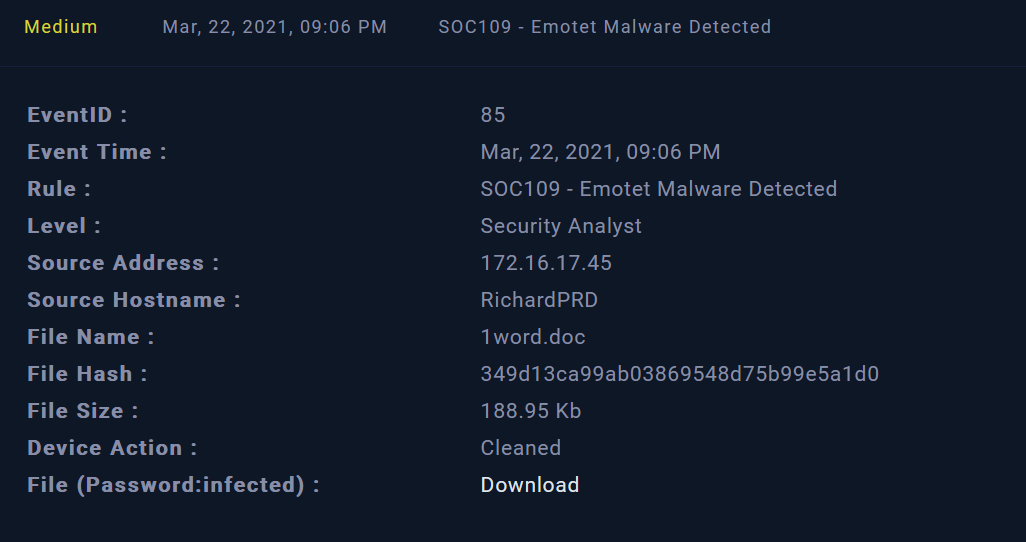
We start our investigation by reviewing the alert’s information about the event occurred on March 22,2021.
More information about the incident are shown in the screenshot below :
 |
|---|
| incident details |
The alert indicates that the incident is related to RichardPRD endpoint that was infected by the malicious file “1word.doc”.
The infected device is cleaned but we have to conduct further investigations on this incident.
Detection and Analysis
In this phase, our main goal is :
- Define Threat indicator
- Check if malware is quarantined/cleaned
- Analyse the Malware in 3rd party tools and find C2 addresees
- Check if someone requested the C2 address
- Add artifacts
📍 What is Emotet Malware ?
Emotet is a malware that first appeared in 2014 as a banking Trojan and spreads mainly via phishing emails attachments and links. The main goal of Emotet is to extract sensitive information from the victim’s computer.
According to Kaspersky, Emotet evolved from a banking Trojan into a Dropper, which means that the Trojan reloads malware onto devices. These are then responsible for the actual damage to the system.
In most cases the following programs were ‘dropped’:
- Trickster (also known as TrickLoader and TrickBot): A banking Trojan that attempts to gain access to the login data of bank accounts.
- Ryuk : An Encryption Trojan - also known as a Cryptotrojan or Ransomware - encrypts data and thus blocks the user of the computer from accessing this data or the entire system.
Now, it’s time to analyze the malicious file called 1word.doc related to Emotet malware.
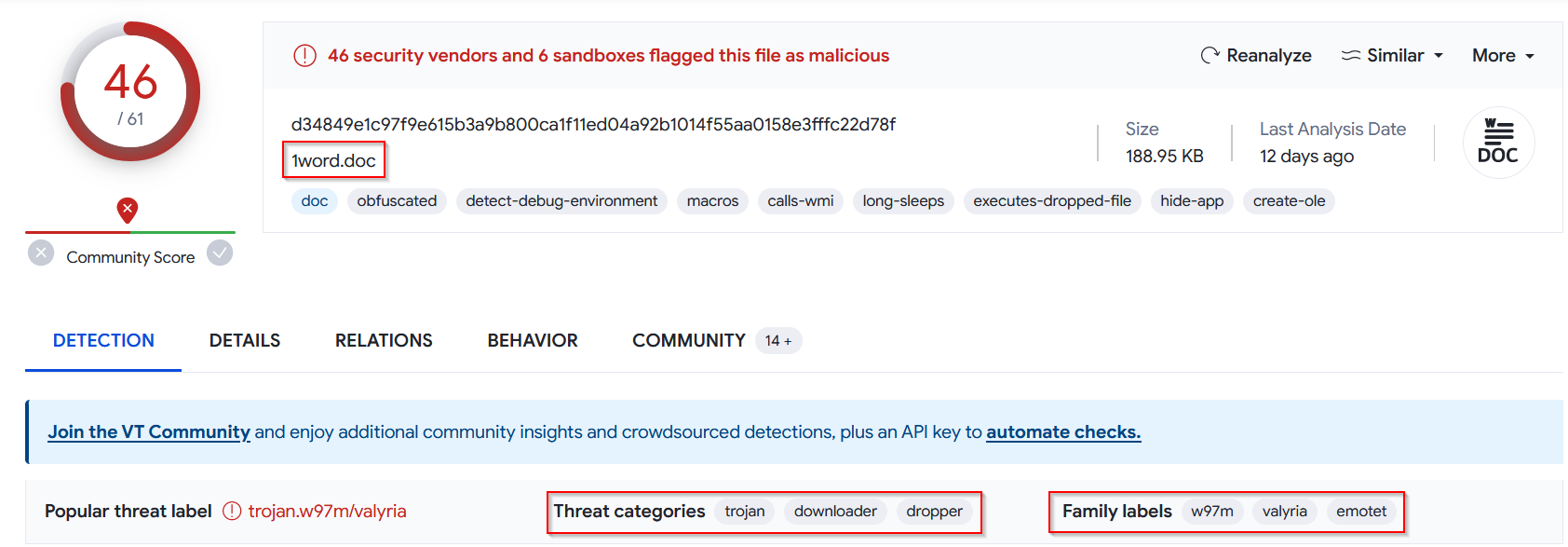
📍 Analysis with VirusTotal :
 |
|---|
| VirusTotal result |
The file 1word.doc is identified as malicious by VT according to 46 security vendors and 6 sandboxes as shown in the screenshot above.
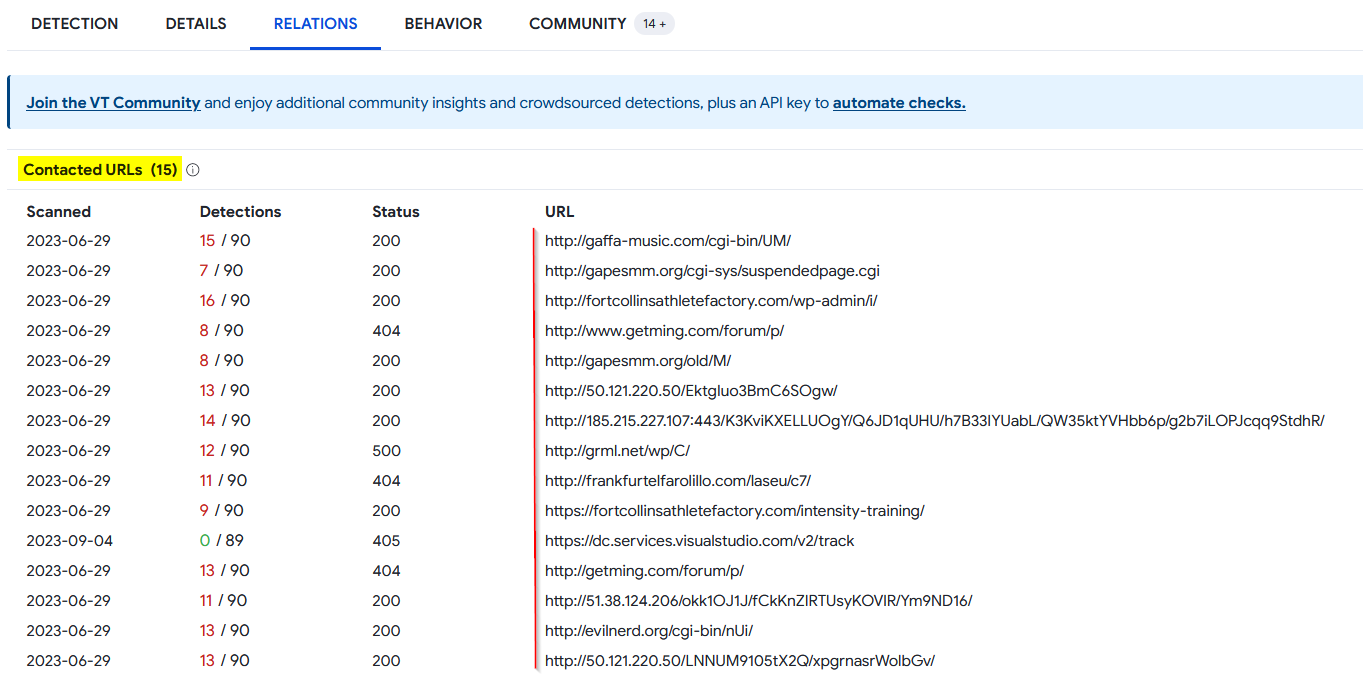
In the Relations tab we can see all the malicious URLs related to Emotet malware, malicious domains and C2 addresse :
Malicious URLs :
 |
|---|
| Malicious URLs related to Emotet |
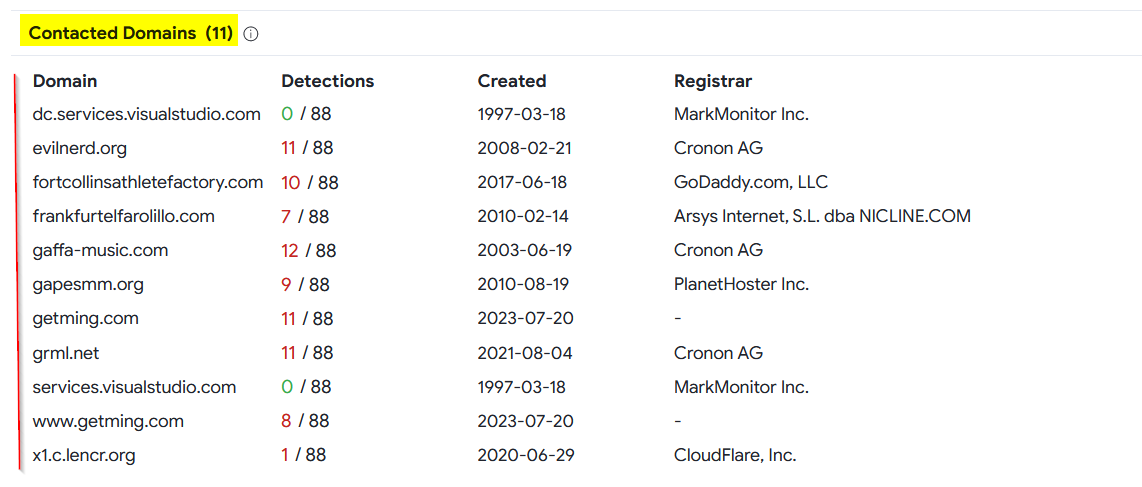
Malicious Domains :
 |
|---|
| Malicious domains related to Emotet |
Malicious IP addresses :
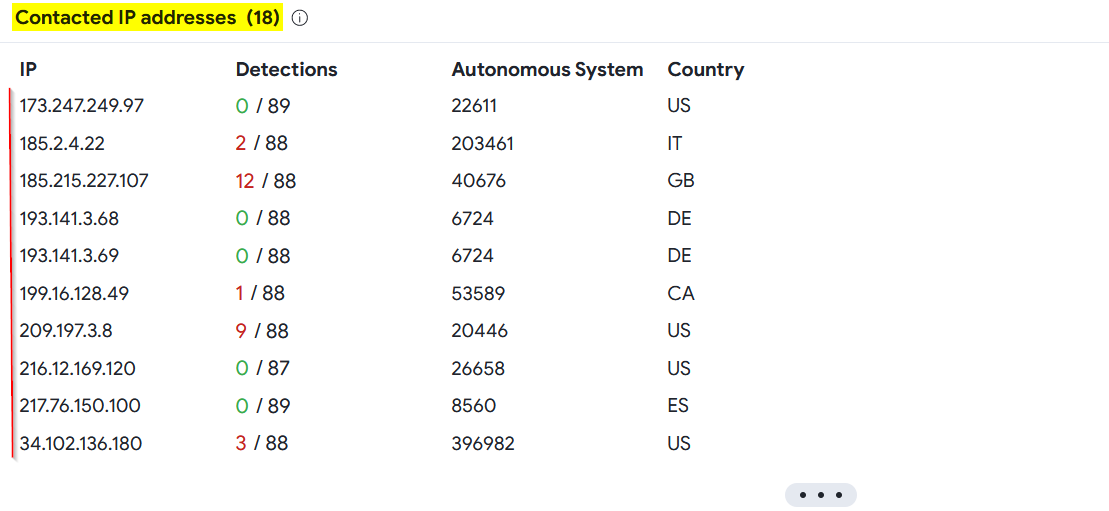 |
|---|
| Malicious IP addresses related to Emotet |
We can take note of theses findings to add them as artifacts in our security playbook.
📍 Analysis with AnyRun :
We uploaded the zip file to AnyRun Malware Sandbox to expand our investigation. And here’s the result :
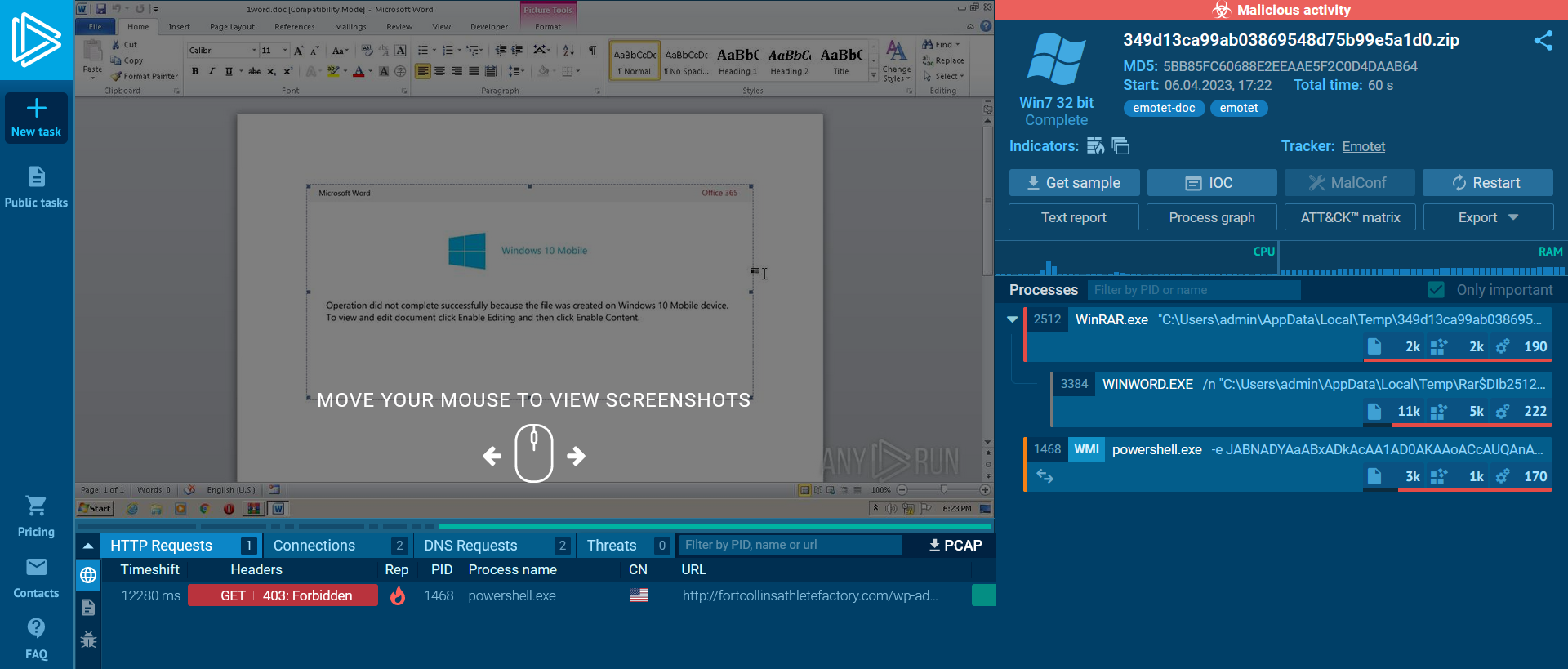 |
|---|
| AnyRun Results |
The file is identified as malicious too.
On the right window of AnyRun we can find all the processes run by Emotet malware once it access the target system :
 |
|---|
| Processes and commands run by Emotet |
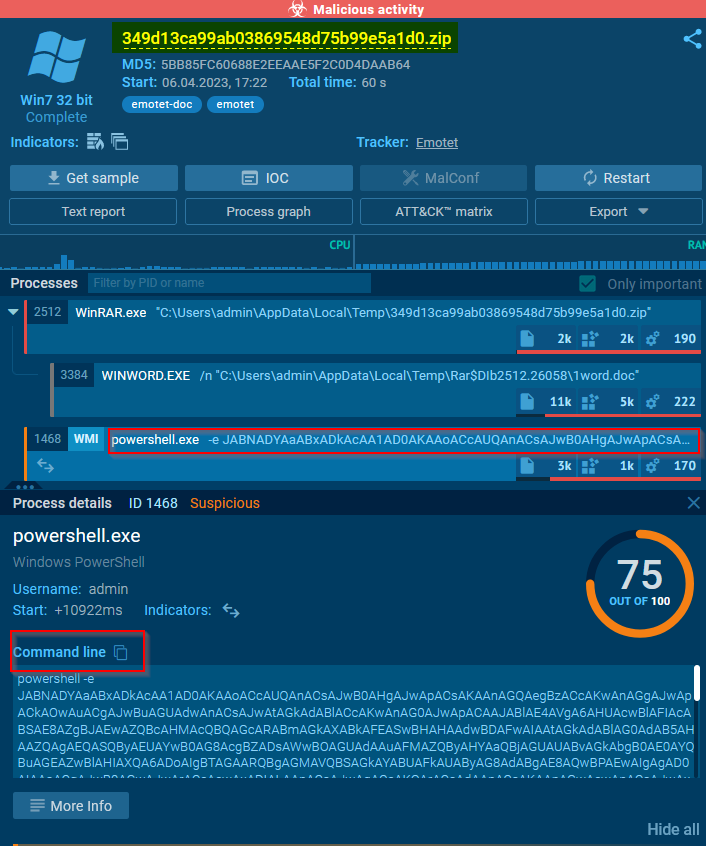
Here in the previous screenshot we notice a powershell command run by Emotet. It’s obviously base64-encoded. Let’s decode it to see result :
 |
|---|
| Powershell command run by Emotet after base64 decode |
The PowerShell command is still obfuscated using ‘.’ to separate every character. We will remove them to see the whole command :
 |
|---|
| Powershell command run by Emotet after null bytes removed |
We can notice the URLs used within the script in the previous screenshot are also separated by “+” character. For example the URL : http:’+’//’+’memtre’+’at’+’.com/TO’+’n9’+’K5’+’1QK1pJ2qI’+’_SKaebFAz which is in fact hxxp://memtreat[.]com/TOn9K51QK1pJ2qI_SKaebFAz/
The same goes for all the URLs used within the command. We will get at the end :
- hxxp://memtreat[.]com/TOn9K51QK1pJ2qI_SKaebFAz/
- hxxp://medongho[.]vn/SVm5yC0s
- hxxp://otojack.co[.]id/wp-content/uploads/xvVQc2RzdDhTWswVa
- hxxp://ptmmf.co[.]id/uNVMPELTQ_ldQ
- hxxp://potlackariet[.]sk/bXfkJ2SeKd7g
These URLs are the C2 URLs used to download the malware.
Artifacts
In this step, we will add artifacts to our EDR Tools to avoid a similar incident in the future. I’ve added primarily the MD5 hash of the malicious file 1word.doc related to Emotet malware :
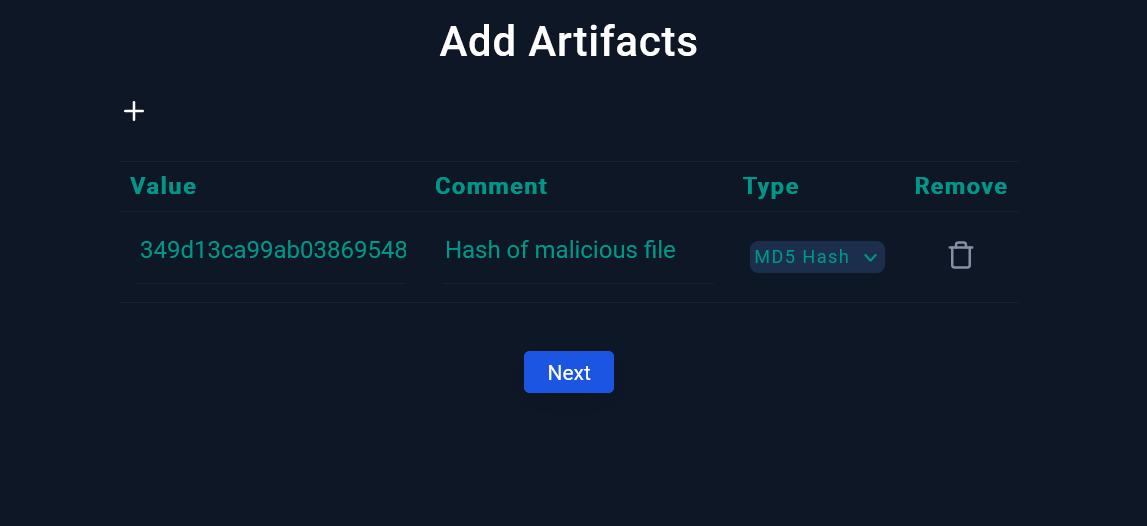 |
|---|
| Adding artifacts |
We can Also add the C2 IP addresses identified previously by VirusTotal as well as the C2 URLs discovered in the Powershell command.
Playbook
As a final step, we will fill the security playbook by answering the following questions :
- Malware quarantined/cleaned? Yes, According to the alert details provided before.
- Analyze the malware. Is it safe or malicious? Malicious
- Tools used during the analysis : VirusTotal, AnyRun Sandbox
- Check If Someone Requested the C2 Malicious addresses are not accessed by anyone after inspecting the log management page.
Close Alert
Finally, the incident is identified as True Positive (TP) and was mitigated successfully. We can close the alert !
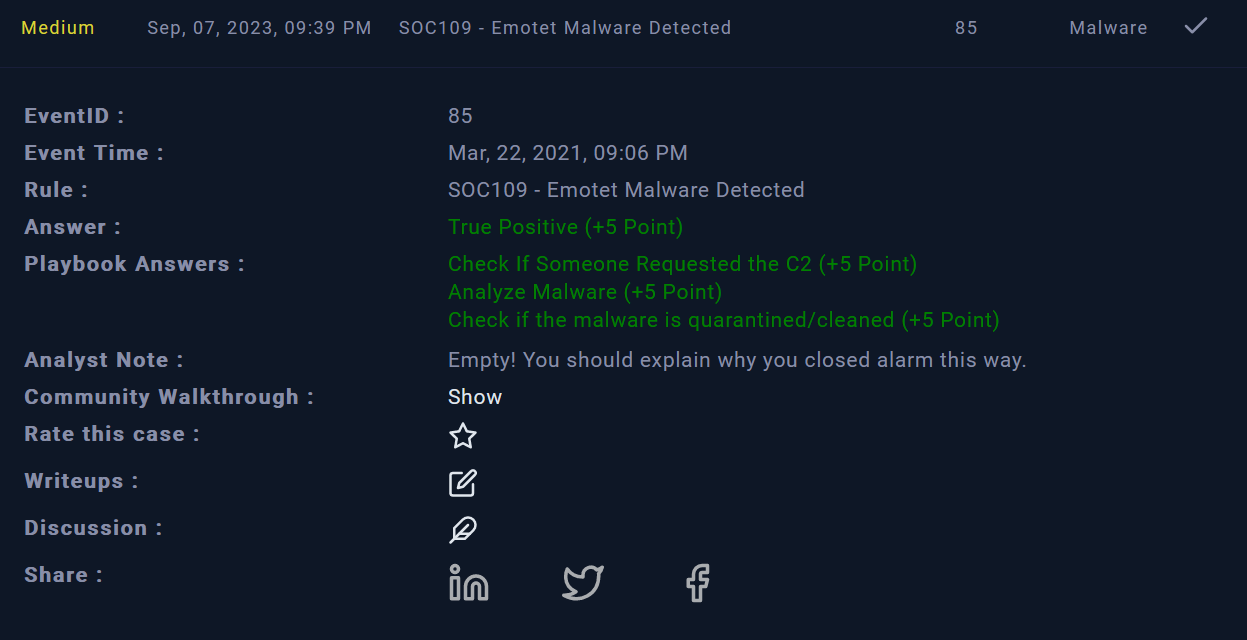 |
|---|
| Alert closed |
![]()
“To beat a hacker, you have to think like a hacker” 💙