Investigating a phishing email alert with malicious excel document
Today we will be investigating a real phishing attack scenario on LetsDefend plateform. This writeup will explain how to respond to a security alert on SOC department following the incident response steps.
Let’s start 🎯
Security Alert
Our investigation starts from the monitoring page by taking ownership of the phishing alert for the detection and analysis phase.
we will be provided by the incident details such as event ID, sender and receiver email address, the subject and much more as shown in the screenshot below :
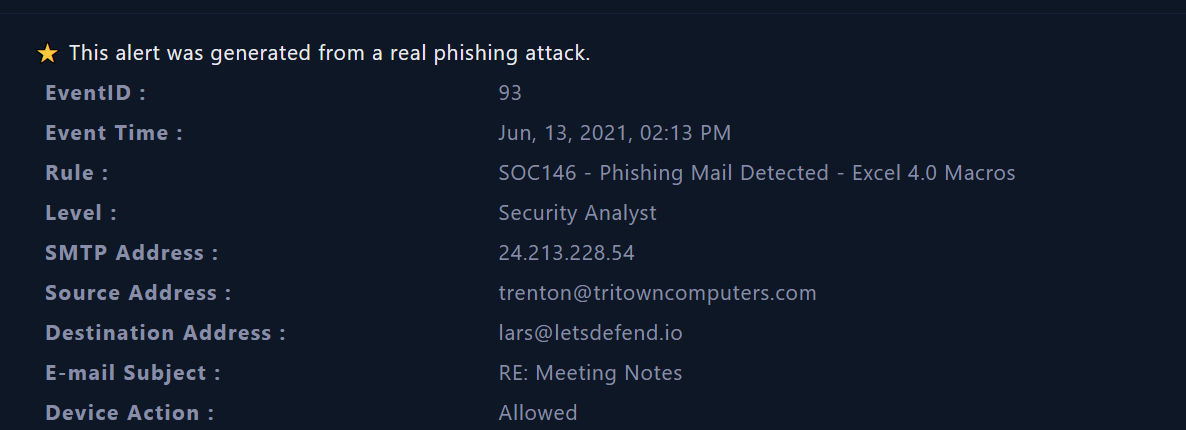 |
|---|
| incident details |
It’s time to start the analysis and detection phase !
Detection and Analysis
In this phase, we have to :
- Analyse the email sent to Lars
- Check for URLs and files sent as an email attachment
- Use VirusTotal to decide whether the files are malicious or not
- If so, we have to investigate if Lars has opened and executed the malicious file
The sender is : trenton@tritowncomputers[.]com
The recipient is : lars@letsdefend[.]com
The attachment(s): 11f44531fb088d31307d87b01e8eabff.zip
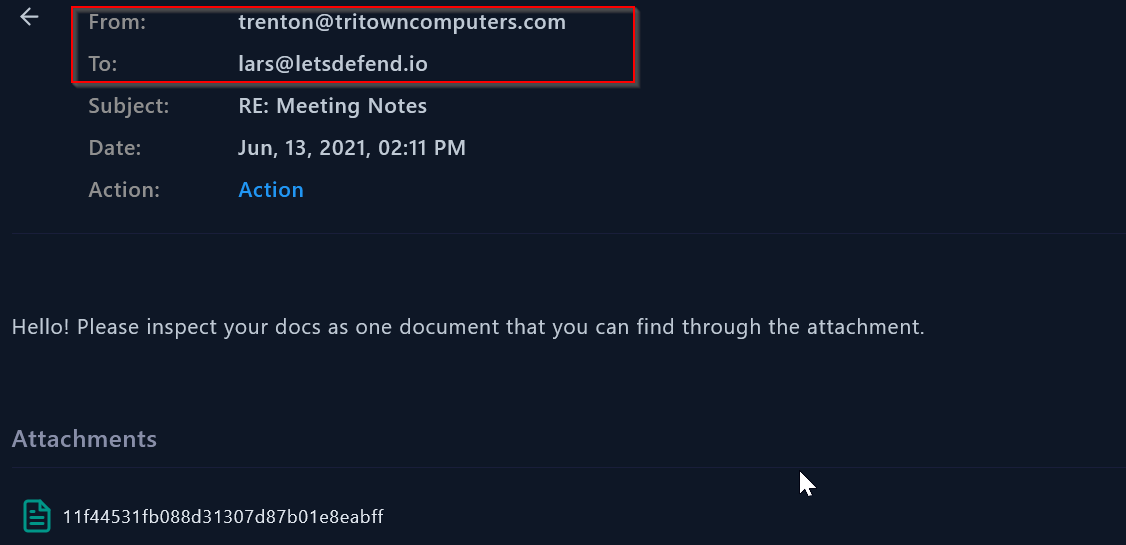 |
|---|
| Email sender,receiver and attachment |
Next, we will download the attachment and unzip it in a safe environment (in my case I download it into my kali linux virtual machine, separated from my local environment).
The attachment contains 2 dll files and 1 excel document :
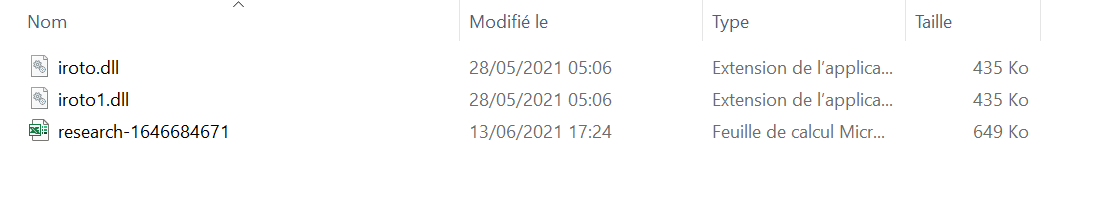 |
|---|
| Attachment files |
📍 VirusTotal :
First dll file :
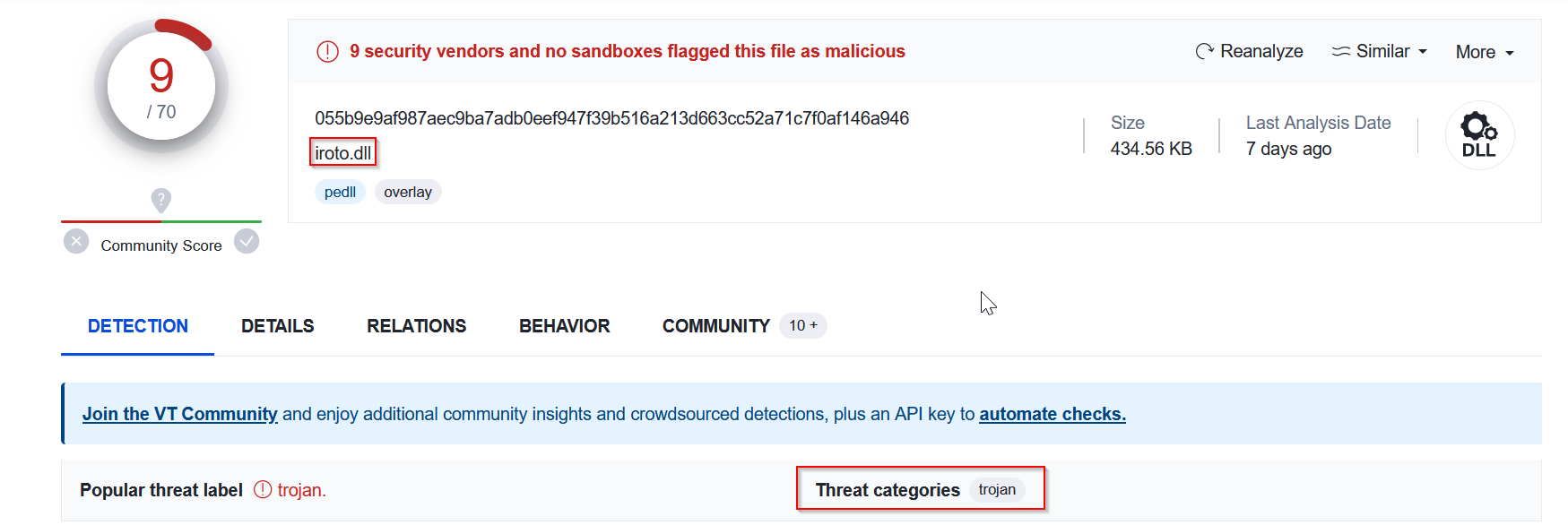 |
|---|
| iroto.dll file |
Second dll file :
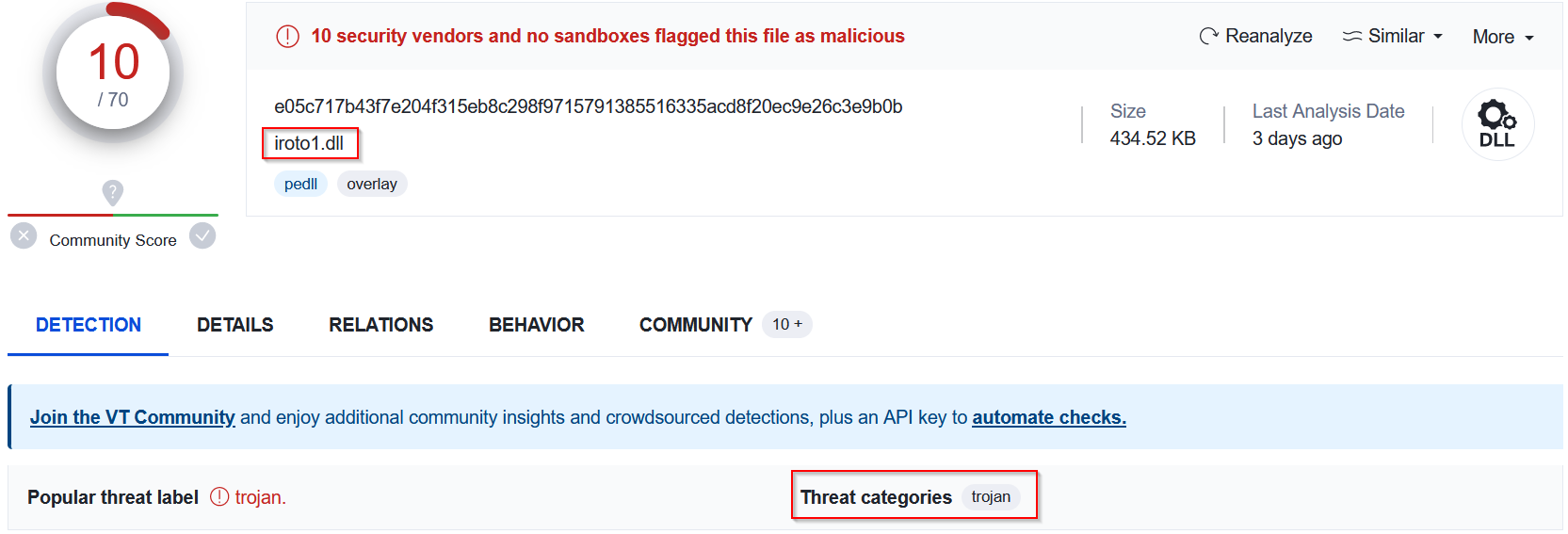 |
|---|
| iroto1.dll file |
Excel document :
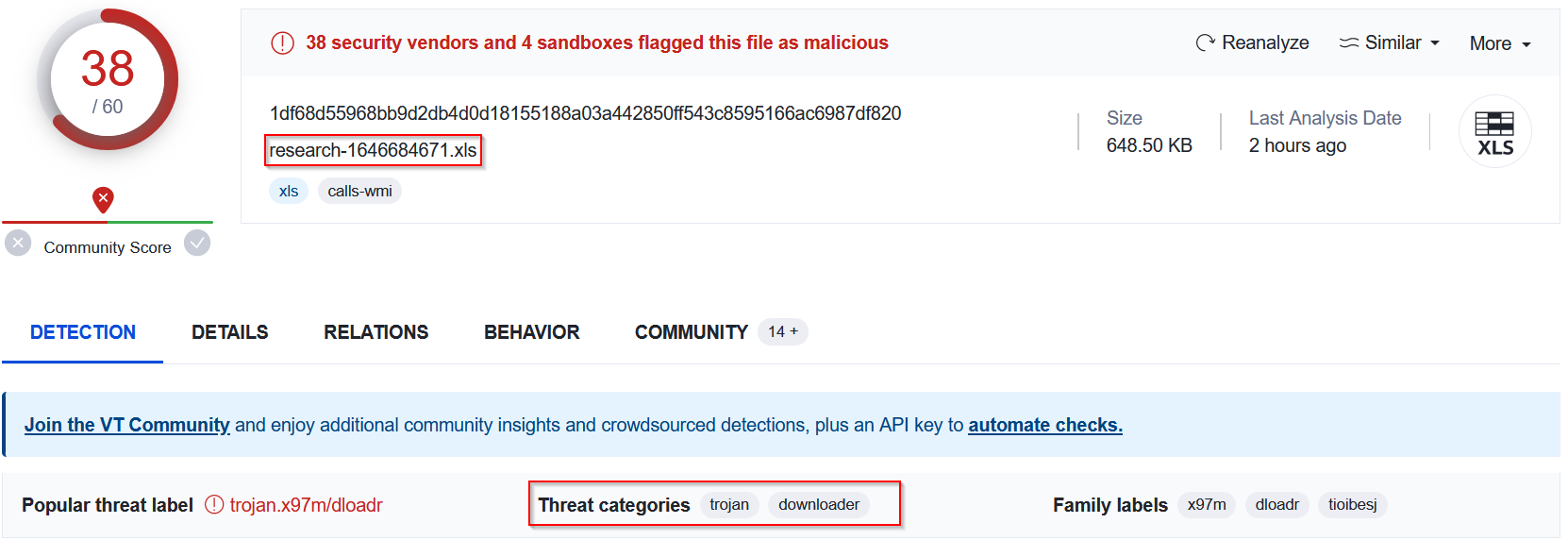 |
|---|
| xls document |
We can conclude that all the files sent within the attachment are malicious as they are identified by VirusTotal as Trojans.
📍 Are the malicious files accessed by the user?
First we have to determine the IP address of the user machine and search for it in the log management tab to see their network activities.
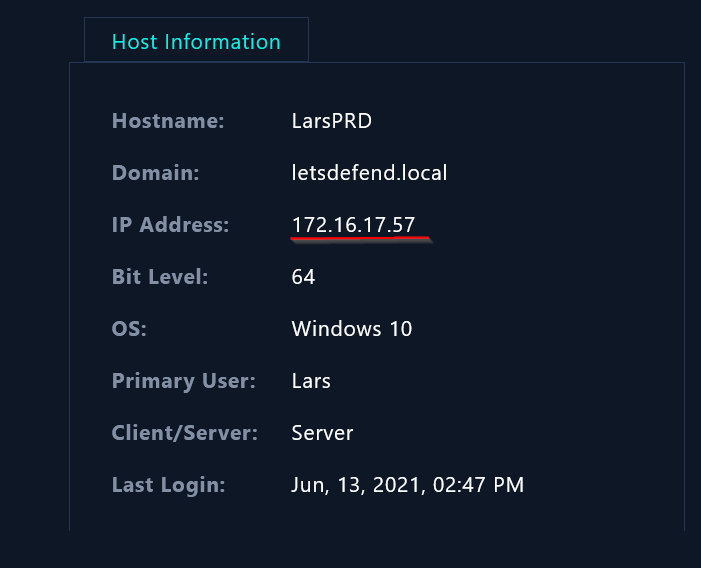 |
|---|
| IP address of user Lars |
We will find 2 events in the log management related to the user Lars at the same day when the phishing email was delivered.
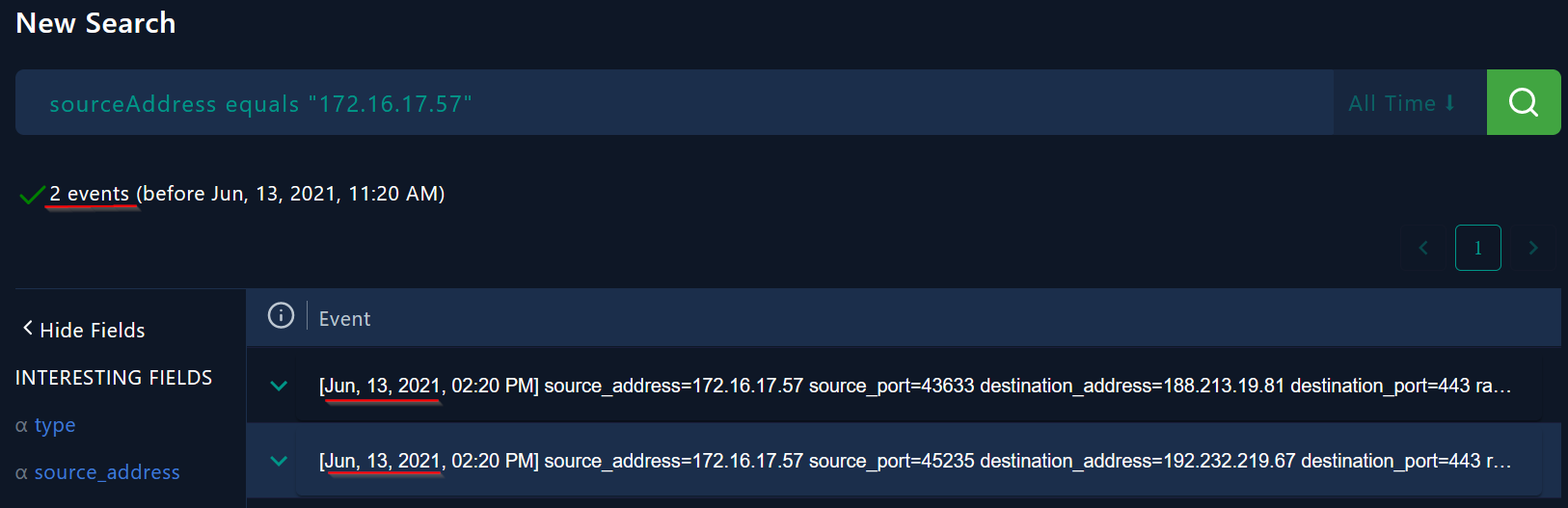 |
|---|
| the user’s logs |
Before starting analyzing the logs details we have to determine the malicious URLs related to the malicious attachment which are identified by VirusTotal as shown in the screenshot below :
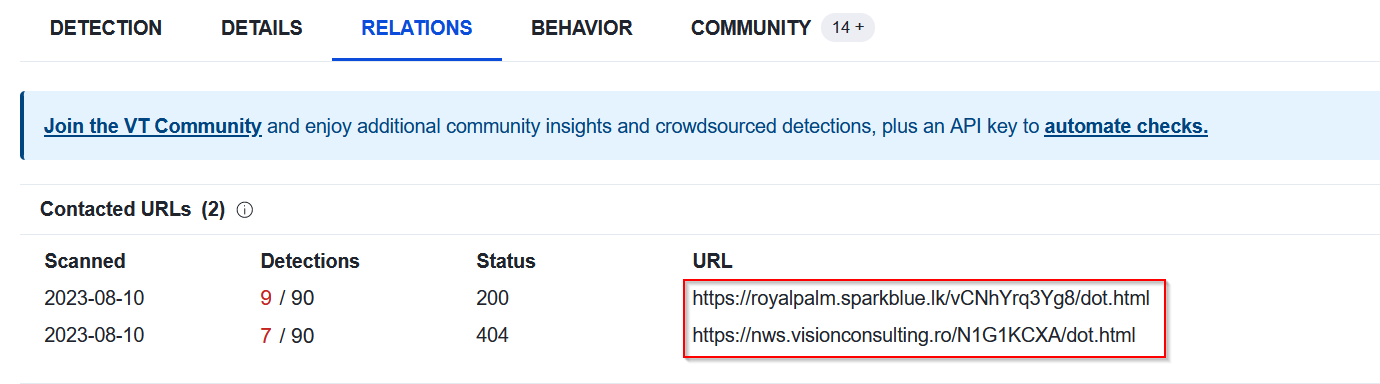 |
|---|
| malicious URLs |
When investigating these 2 log events, we will find the following : First log event :
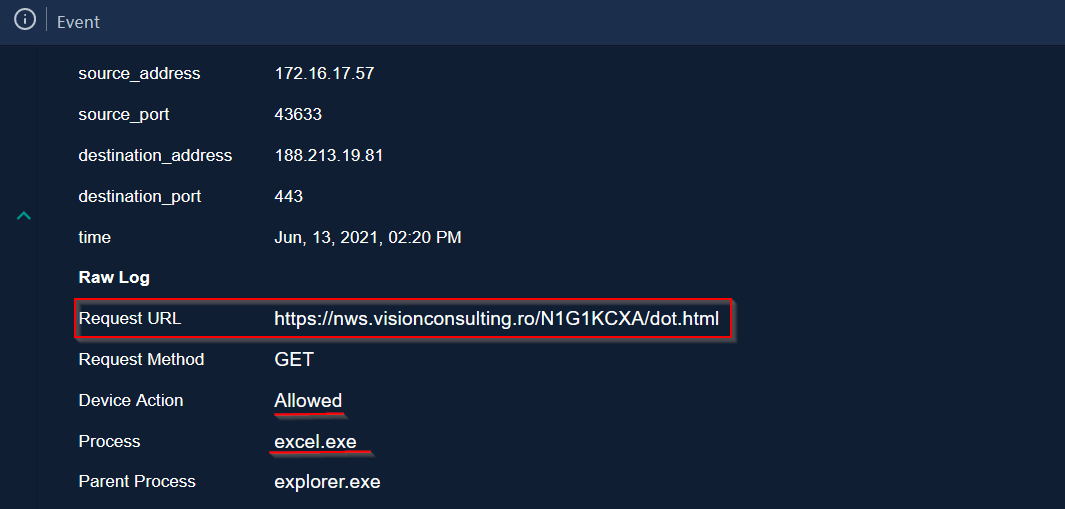 |
|---|
| First Malicious URL has been visited by the user |
Second log event :
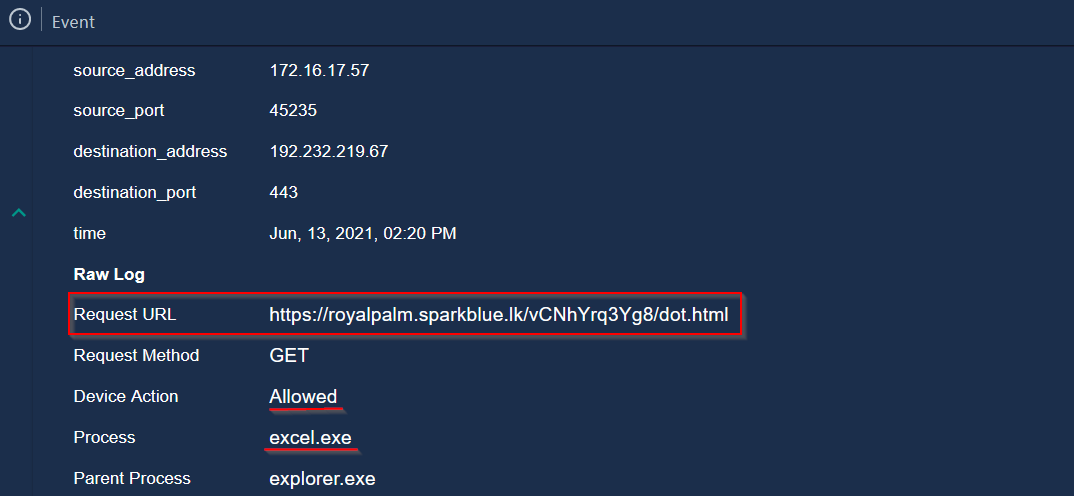 |
|---|
| Second Malicious URL has been visited by the user |
We can confirm that the user Lars has opened the attachment and has visited the websites that are connected to the malware.
Containment
The purpose of the containment phase is to halt the effects of the incident before it can cause further damage. To do so, we will contain and isolate the user’s machine from the environment.
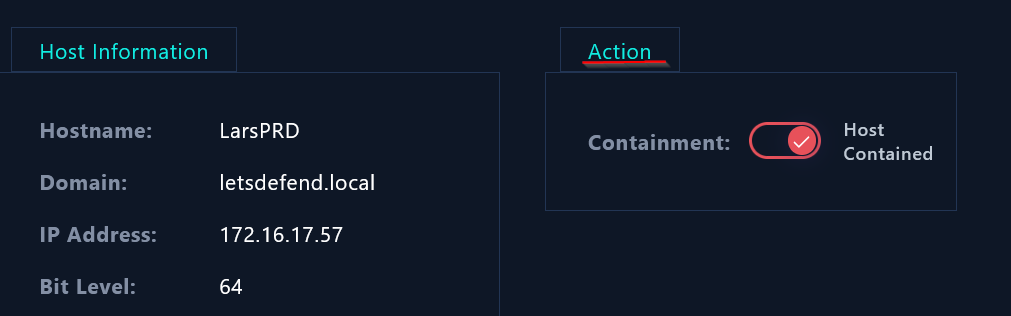 |
|---|
| The containment of the infected machine |
Artifacts
In this step, we will add artifacts to our EDR to avoid a similar incident in the future. Artifacts are residual traces left behind by the actions of attackers or malicious actors within a computer system or network.
In our case, the artifacts that sould be added are :
- The 2 malicious URLs identified by VirusTotal
- The MD5 hash of dll files sent within the attachment
- The MD5 hasj of the excel document
- The email address of the sender (Attacker)
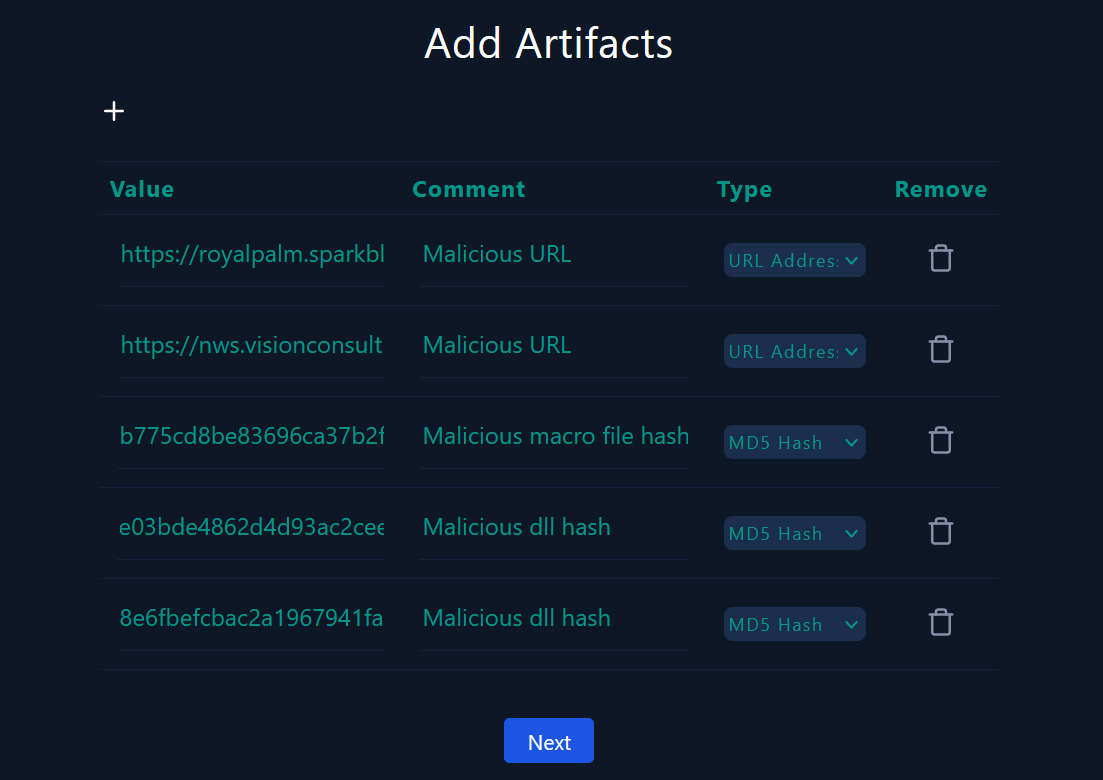 |
|---|
| Adding artifacts |
Playbook
A security playbook is a list of required steps and actions needed to successfully respond to any incident or threat.
We will answer the following questions :
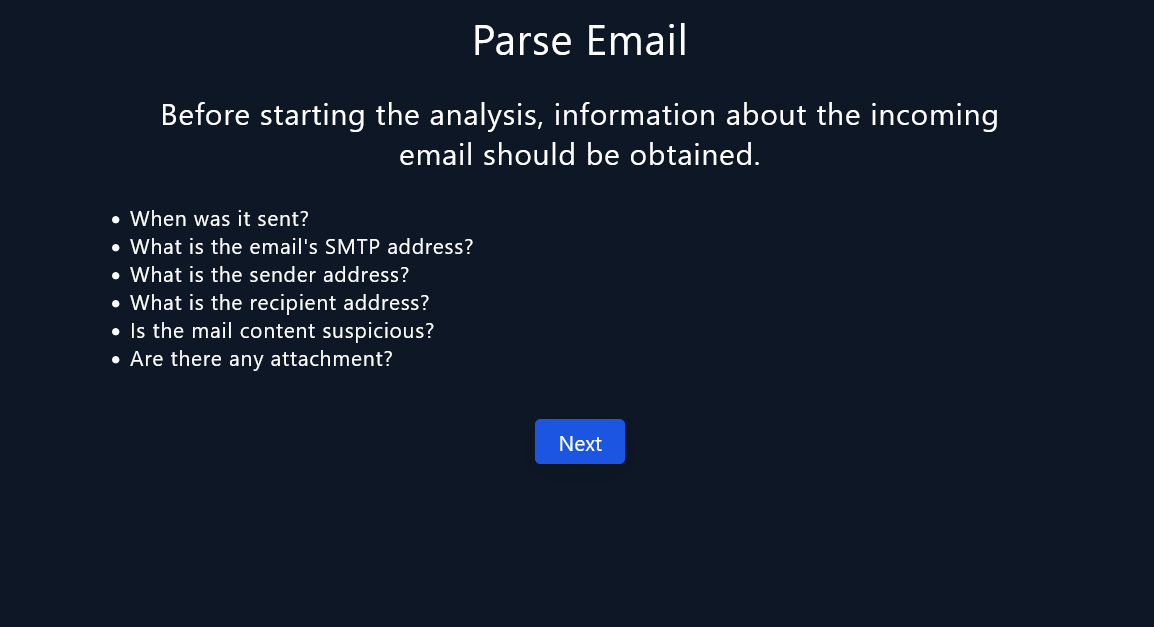 |
|---|
| Playbook |
- When was it sent? June 13, 2021 2:11 P.M
- What is the email’s SMTP address? 24.213.228.54
- What is the sender address? trenton@tritowncomputers[.]com
- What is the recipient address? lars@letsdefend.ioM
- Is the mail content suspicious? Yes.
- Are there any attachment? Yes.
- Was email delivered to user? Yes.
- Was the infected machine contained? Yes.
Close Alert
Finally, the incident is identified as True Positive (TP) and was mitigated successfully. We can close the alert !
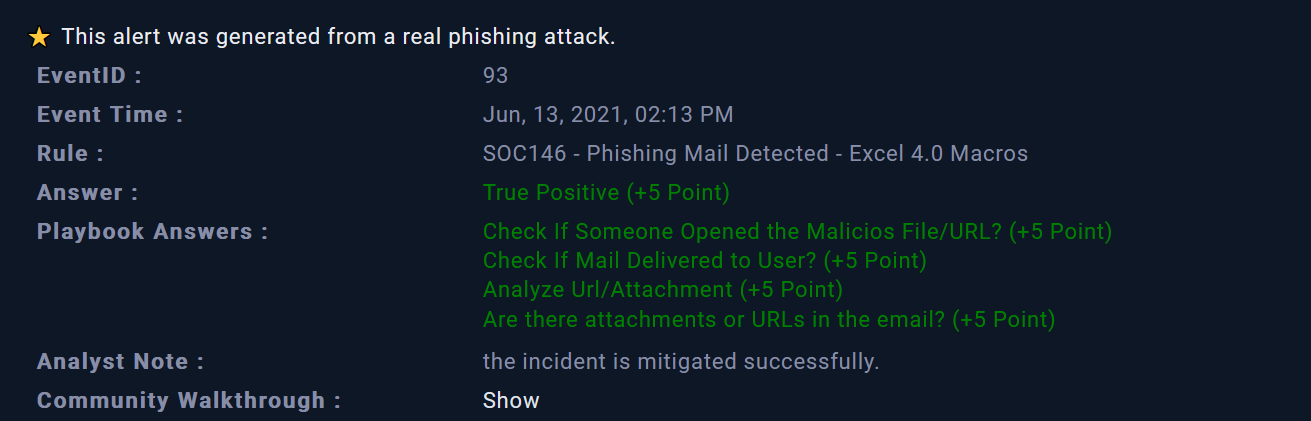 |
|---|
| Alert closed |
![]()
“To beat a hacker, you have to think like a hacker” 💙