Learn how to identify threats and attacks via network analysis using wireshark
Wireshark Overview
What is Wireshark?
Wireshark is a network packet analyzer. A network packet analyzer presents captured packet data in as much detail as possible. (Wireshark.org)
It is a free open source tool that analyzes network traffic in real-time for Windows, Mac, Unix, and Linux systems by capturing packets from a network interface or reading packets from a capture file.
Wireshark Core Features
- Deep inspection of hundreds of protocols
- Live capture
- Offline analysis
- Support multiple OS (Windows, Linux, Mac OS)
- Powerful packet filters
- Colorize packet display based on filters
- Create various statistics
- … and much more!
Wireshark Options
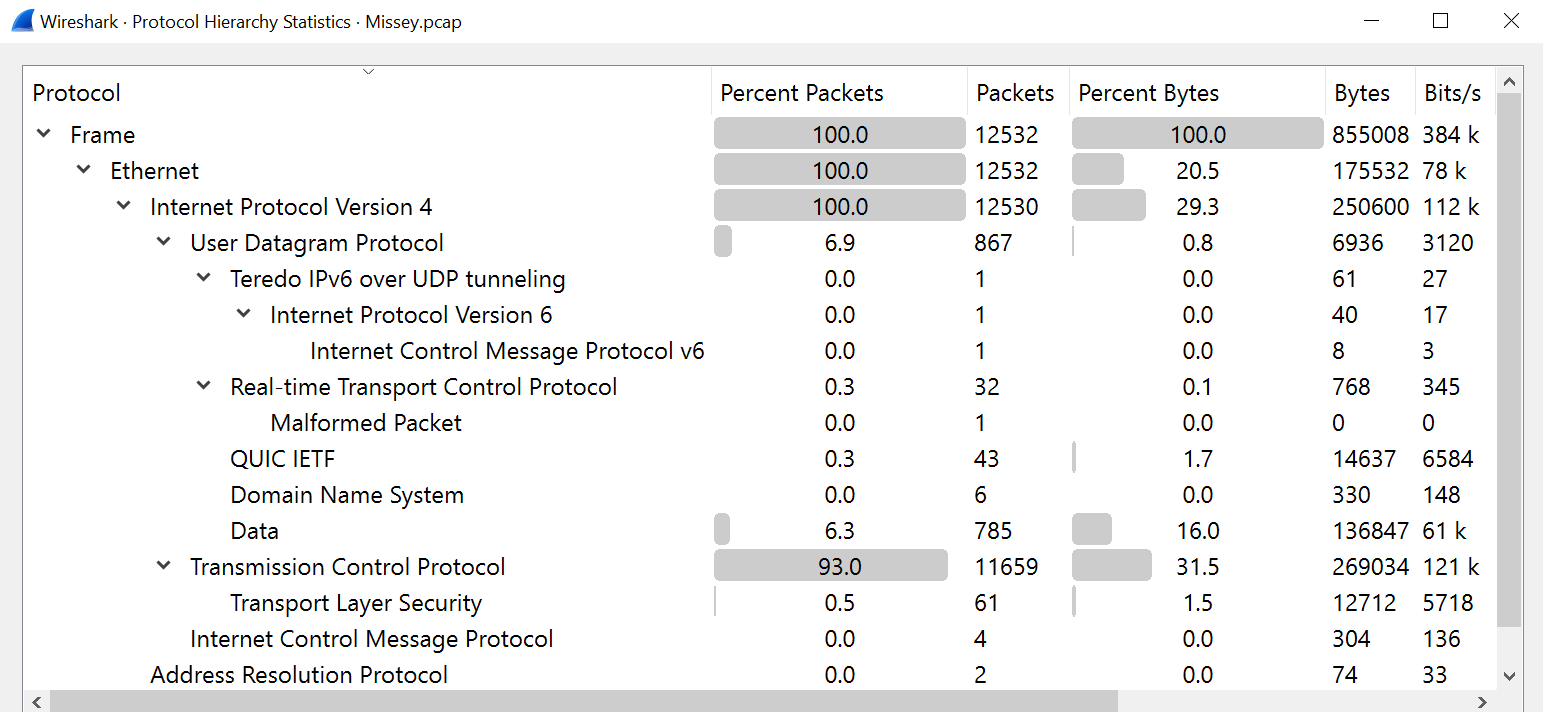
📌 Protocol Hierarchy:
Generates a protocol hierarchy chart that contains the statistical values of each protocol (Percent Packets and Percent Bytes):
 |
|---|
| Protocol Hierarchy Window |
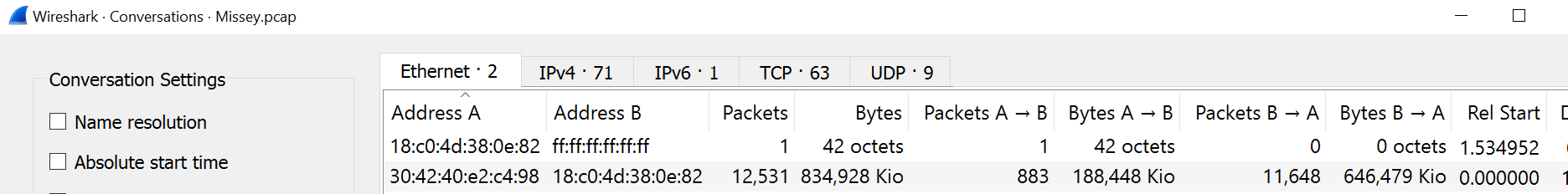
📌 Conversations:
This window shows all the established conversations between two endpoints alongside with other info like packet count, bytes, duration, etc. This option provides the list of the conversations in five base formats; ethernet, IPv4, IPv6, TCP and UDP. Thus analysts can identify all conversations and contact endpoints for the event of interest.
 |
|---|
| Conversation Window |
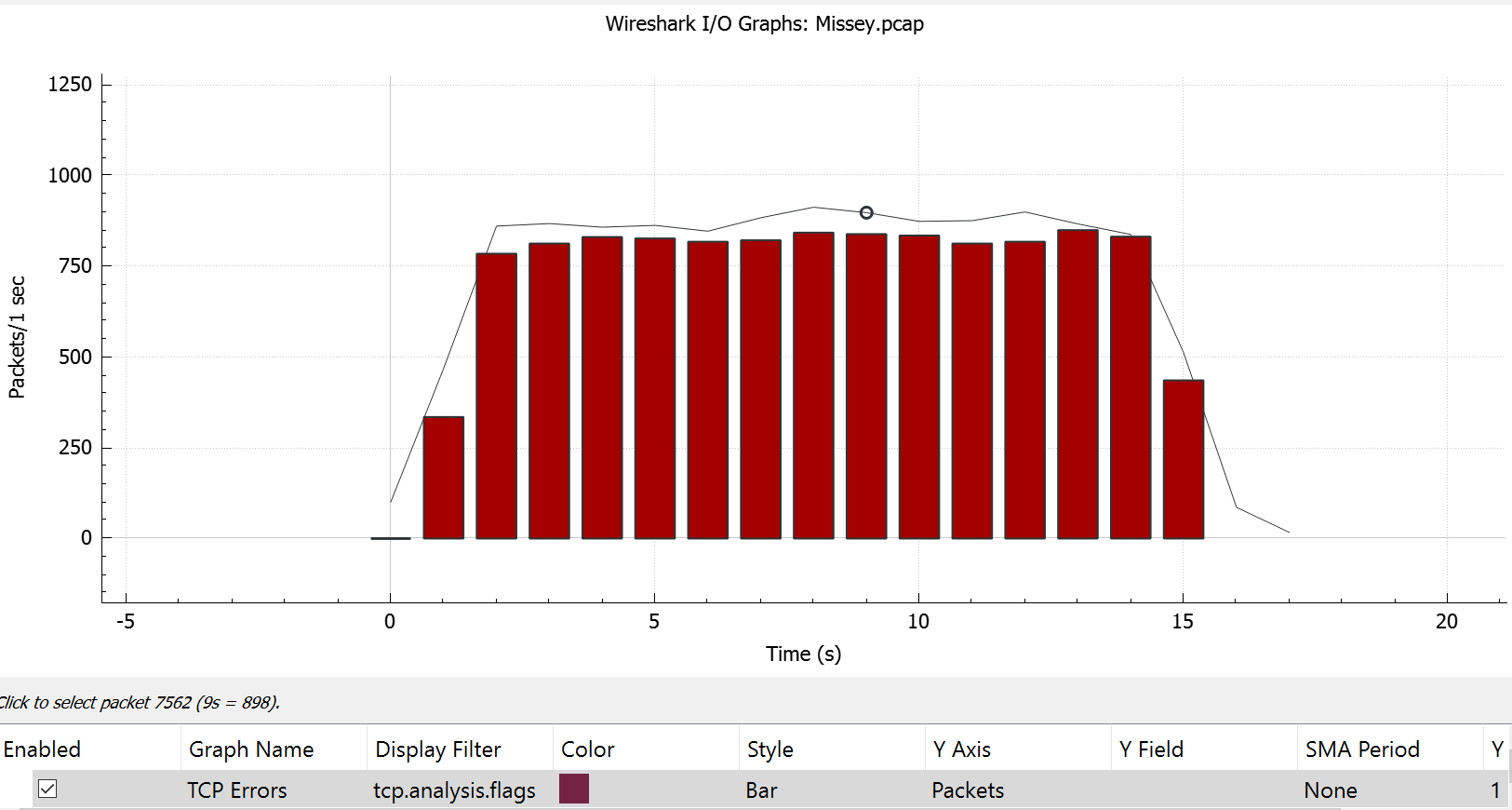
📌 I/O Graph:
A Wireshark I/O Graph is one of the basic diagrams that is created using the packets present in the capture file. Useful for viewing packet and log data in a variety of ways.
 |
|---|
| I/O Graph Window |
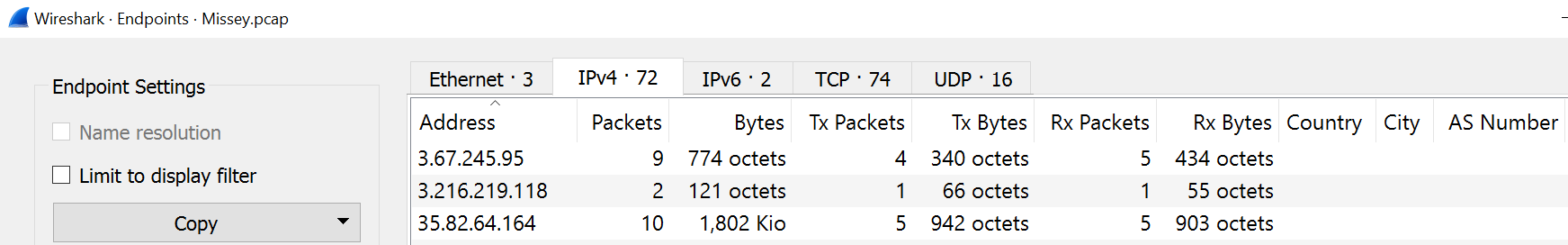
📌 Endpoints:
This window shows statistics about the endpoints captured. The endpoints option is similar to the conversations option. The only difference is that this option provides unique information for a single information field (Ethernet, IPv4, IPv6, TCP and UDP ). Thus analysts can identify the unique endpoints in the capture file and use it for the event of interest
 |
|---|
| Endpoints Window |
For more options, you can visit wireshark official documentation
Filters
| Filter | Symbol | Example |
|---|---|---|
| equal | == | ip.src == 192.168.12.2 |
| not equal | != | ip.src != 192.168.12.2 |
| AND | && | ip.src==10.0.0.1 and tcp.flags.syn |
| OR | || | ip.src==10.0.0.1 or tcp.flags.syn |
| greater than | > | ip.ttl > 250 |
| less than | < | frame.len < 100 |
| Protocol | Filter | Description |
|---|---|---|
| ARP | - Arp.dst.hw | - Hardware Address |
| HTTP | - http.response.code == 200 - http.request.method == "GET" |
- packets with HTTP response code "200" - Show all HTTP GET requests |
| FTP | - ftp.command - ftp.active.cip |
- filter FTP commands - filter active IP address |
| TCP | - tcp.port == 80 - tcp.ack |
- Show all TCP packets with port 80 - Show acknowledgement packets |
| UDP | - udp.port == 53 - udp.srcport== 1234 |
- Show all UDP packets with port 53 - Show all UDP packets originating from port 1234 |
| DNS | - dns.flags.response == 0 - dns.flags.response == 1 - dns.qry.type == 1 |
- Show all DNS requests - Show all DNS responses - Show all DNS "A" records |
| ICMP | - icmp.code - icmp.data_time - icmp.type |
- filter ICMP code - filter ICMP data timestamp - filter ICMP packets types |
Advanced Filtering
| Filter | Description | Example |
|---|---|---|
| contains | Search a value inside packets | - http.server contains "Apache" => Find all "Apache" servers |
| matches | Search a pattern of a regular expression | - http.host matches "\.(php|html)" => Find all .php and .html pages |
| in | Search a value or field inside of a specific scope/range | - tcp.port in {80 443 8080} => Find all packets that use ports 80, 443 or 8080 |
Hunting with Wireshark
TCP Malicious Traffic
There are multiple patterns for malicious TCP traffic, for example, we can hunt for port scans by searching for:
- SYN without SYN/ACK.
- SYN/ACK without SYN before.
- ACK without a SYN/ACK before.
📍 Nmap TCP SYN Scans : Usually have a size less than or equal to 1024 bytes as the request is not finished and it doesn’t expect to receive data
↪ tcp.flags.syn==1 and tcp.flags.ack==0 and tcp.window_size <= 1024
📍 Nmap TCP Connect Scan : Usually has a windows size larger than 1024 bytes as the request expects some data due to the nature of the protocol
↪ tcp.flags.syn==1 and tcp.flags.ack==0 and tcp.window_size > 1024
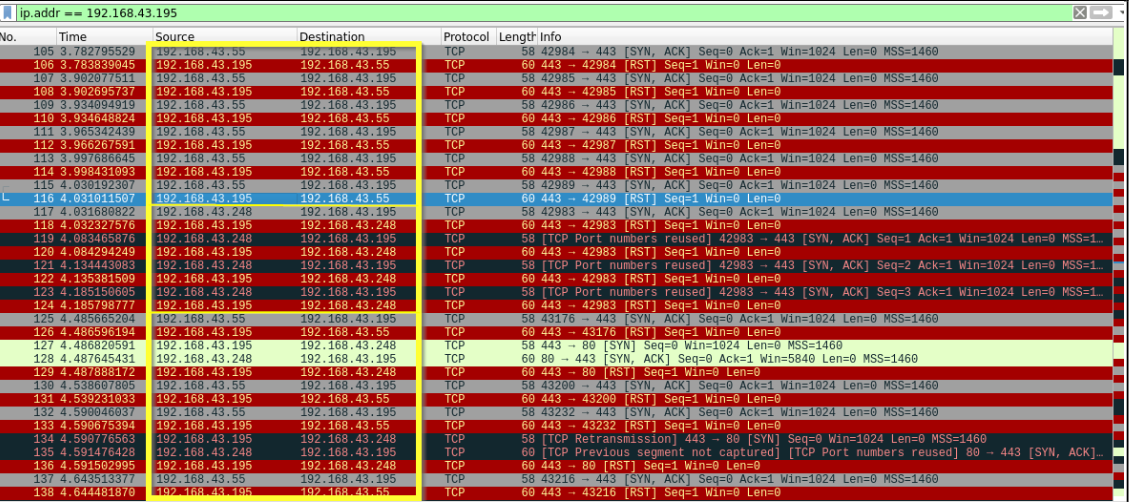
📍 Nmap Zombie Scan : It is a TCP port Scan method used to send a spoofed source address to a computer to find out what services are available and offers blind scanning of a remote host. This is accomplished by impersonating another computer. No packet is sent from its own IP address, instead, another host is used called Zombie.
 |
|---|
| Nmap Zombie Scan |
The screenshot below shows the phases in which scan happens :
- The first slot show communication between attacker and zombie.
- The second slot is where the actual scan takes place. The zombie communicates with the target.
- The third slot is communication between zombie and attacker to verify port status.
HTTP Malicious Traffic
HTTP traffic should be monitored carefully because various attacks are conducted over HTTP.
For example, signs of SQL Injection attacks or XSS can be shown in HTTP traffic. Also, web shells and exploits can be uploaded over HTTP.
📍 Hunting Nmap in HTTP traffic : http.user_agent contains "nmap"
DNS Malicious Traffic
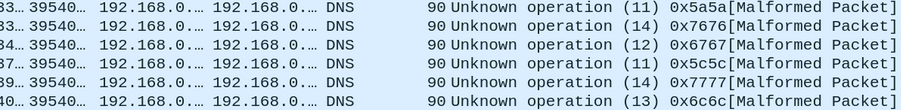
📍 DNS Exfiltration :
Data can be exfiltrated using DNS in many formats, for example, data chunks can be included with the subdomains for a domain name or can be transferred inside malformed packets.
 |
|---|
| DNS Exfiltration |
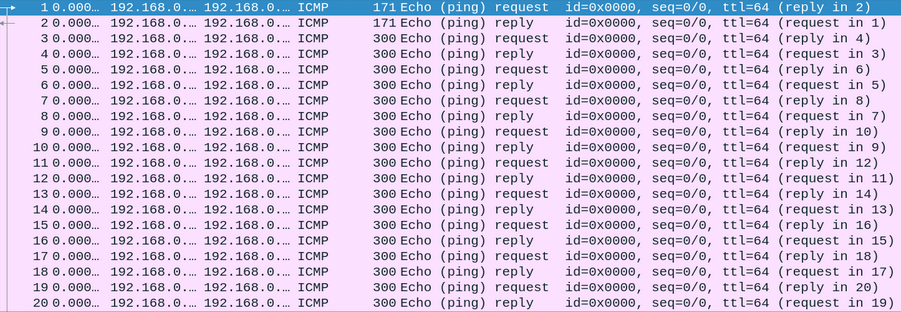
Exfiltration through ICMP
ICMP is a supporting protocol in the Internet protocol suite and is widely known for its applications such as ping or traceroute. Malicious actors can use ICMP to exfiltrate data, by taking advantage of organizations that allow outbound ICMP traffic.
 |
|---|
| ICMP Exfiltration |
Hunt cleartext credentials :
Some Wireshark dissectors (FTP, HTTP, IMAP, pop and SMTP) are programmed to extract cleartext passwords from the capture file. You can view detected credentials using Wireshark under the Tools --> Credentials menu. This feature works only after specific versions of Wireshark (v3.1 and later). Since the feature works only with particular protocols, it is suggested to have manual checks and not entirely rely on this feature to decide if there is a cleartext credential in the traffic.
Example: Log4j Hunting
What is Log4j Vulnerability
Log4j is an open-source logging framework maintained by Apache used to log messages within software and has the ability to communicate with other services on a system. This communication functionality is where the vulnerability exists, providing an opening for an attacker to inject malicious code into the logs so it can be executed on the system.
This zero-day vulnerability in the Apache Log4j logging utility has been allowing easy-to-exploit remote code execution (RCE). Attackers can use this security vulnerability in the Java logging library to insert text into log messages that load the code from a remote server.
💡 The targeted server by attackers can execute a code via calls to the Java Naming and Directory Interface (JNDI), which connects its interface with several services such as Lightweight Directory Access Protocol (LDAP), Domain Name Service (DNS), Java’s Remote Interface (RMI). Attackers will then exploit LDAP, DNS, RMI, and URLs by redirecting to an external server.
Wireshark Filters for Log4j Hunting
http.request.method == "POST"(ip contains "jndi") or (ip contains "Exploit")(frame contains "jndi") or (frame contains "Exploit")(http.user_agent contains "$") or (http.user_agent contains "==")
Conclusion
Wireshark is a great tool for Security analysts, Threat hunters and all professionals in general to identify cyber network attacks and conduct threat hunt at the packet level. This can be done starting from network scans hunting, next discovering Web attacks through malicious HTTP traffic and data exfiltration. And last, discover how to spot indicators of compromise in case of malware infections.
“To beat a hacker, you have to think like a hacker” 💙
![]()



