Discover how you can identify threats in a Windows environment.
Powershell Overview
Windows PowerShell is a command-line shell and scripting language that allows developers, IT admins, and DevOps professionals to automate tasks and configurations using code.
Powershell works with objects; in fact, everything in PowerShell is an object. These objects represent attributes (properties) or instructions (methods).
PowerShell manipulates objects with four different types of commands which are:
📍 Cmdlets: – Pronounced as command-lets – , They are considered the basic single-function commands. A cmdlet typically exists as a small script that is intended to perform a single specific function such as coping files and changing directories.
There are hundreds of cmdlets available by default under today’s PowerShell like:
Get-Help: get more information about a desired cmdletGet-Location: get the current directorySet-Location: change the current directoryGet-ChildItem: list items in a directoryCopy-Item: Copy filesMove-Item: move a file- … and much more !!
📍 Functions: Unlike cmdlets, functions are written in PowerShell language. They are a sequence of instructions that are formed and are to be achieved simply by invoking them.
↪ Example of powershell function that return a message passed in parameter :
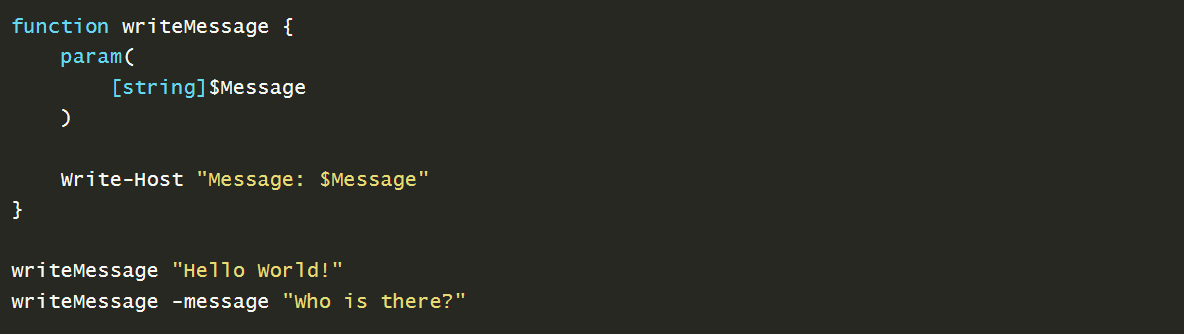 |
|---|
| Powershell Function With Parameter |
📍 Scripts: PowerShell script is a plain text file that contains one or more PowerShell commands. PowerShell scripts are written with cmdlets and have a .ps1 file extension.
Running a script is a lot like running a cmdlet.
↪ Example of Powershell script that turn on Hyper -V on Windows:
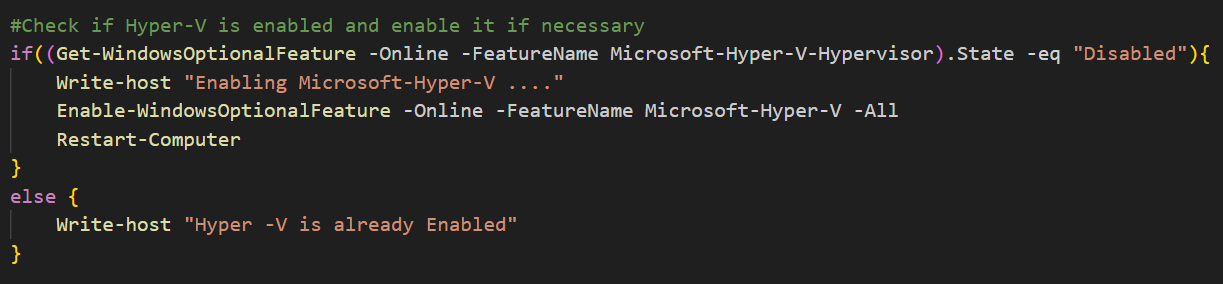 |
|---|
| Powershell Script |
📍 Executable commands: They are commands used in running executable files. There are three commands used in running .exe files:
- The first one is
start-processcmdlet. For exampleStart-Process -FilePath "notepad.exe" - The second one is with the
Invoke-expressioncommand - The third option is typing
.\before the file’s name.
Poweshell Hunting Commands
Schedule Tasks Commands
Get-ScheduledTask: This cmdlet gets the task definition object of a scheduled task that is registered on a computer.
| Command | Description | Example |
|---|---|---|
| Get-ScheduledTask -TaskName "Name” | Get a scheduled task definition object | Get-ScheduledTask -TaskName "SystemScan" |
| Get-ScheduledTask -TaskPath "\Path\*" | Get an array of scheduled task definition objects from a specific path | Get-ScheduledTask -TaskPath "\UpdateTasks\*" |
Services Command
Get-Service: This cmdlet gets objects that represent the services on a computer, including running and stopped services.
| Command | Description | Example |
|---|---|---|
| Get-Service "Nam*" | Get services that begin with a search string | Get-Service "wmi*" |
| Get-Service -Displayname "*Name*" | Display services that include a search string | Get-Service -Displayname "*network*" |
| Get-Service | Where-Object {$_.Status -eq "Running"} | Display services that are currently active | Get-Service | Where-Object {$_.Status -eq "Running"} |
| Get-Service "s*" | Sort-Object status | Sort services by property value | Get-Service "s*" | Sort-Object status |
Baseline
A Baseline is a file that holds the base security control, file system state, etc. and it is used to compare the current machine state with the base state that this baseline represents.
The usage of baselines will help you detect anomalies inside your environment, malicious files, processes, etc.
When analyzed with strong detail, baselines make threat detection easier and more accurate.
📍 BaseLining Processes, Services, Tasks:
Get-Process | Select-Object -Property Name > processes.txt
↪ This command will save the Get-Process command output to process.txt fileGet-Scheduledtask | Select-Object TaskName > scheduledtasks.txt
↪ This command will save the Get-Scheduledtask command output to scheduledtasks.txt fileGet-Service | Select-Object -Property Name > services.txt
↪ This command will save the Get-Service command output to services.txt file
📍 Comparing Baselines:
$baseline = Get-Content .\baseline-services.txt
$current = Get-Content .\current-services.txt
Compare-Object $baseline $current
Hunting Web Shells
This command will retrieve the files of a directory recursively then obtain the SHA1 hash of each file and store them in a CSV file.
Now we can use this exported file as a BaseLine for future use when we need to compare our existing files with our BaseLine.
For web shells, we can get a BaseLine of our web server’s directory.
Get-ChildItem -Path PATH -File -Recurse | Get-FileHash -Algorithm SHA1 | Export-Csv C:\EXPORTPATH
After Getting the SHA1 hash of each file, We can use the following script from GitHub to do the comparison between the two CSV files:
Compare-FileHashesList.ps1
Powershell Hunting Tools
Powershell ISE
The Windows PowerShell Integrated Scripting Environment (ISE) is a host application for Windows PowerShell.
In the ISE, you can run commands and write, test, and debug scripts in a single Windows-based graphic user interface.
 |
|---|
| Powershell ISE |
Powershell AMSI
Antimalware Scan Interface (AMSI) was developed by Microsoft to protect users from malware and introduced for the first time in Windows 10. It allows an application to interact with any anti-virus installed on the system and prevent dynamic, script-based malware from executing.
AMSI intercepts PowerShell, JavaScript, VBScript, VBA, or .NET scripts and commands in real time and sends them to the antivirus software for scanning, and this is where you can get the familiar message
“This script contains malicious content and has been blocked by your antivirus software”.
PSHunt
PSHunt is a Powershell Threat Hunting Module designed to scan remote endpoints for indicators of compromise or survey them for more comprehensive information related to state of those systems (active processes, autostarts, configurations, and/or logs).
📍 PSHunt Components/Modules: PSHunt is divided into several modules, functions, and folders. These modules are:
- Scanners
- Surveys
- Discovery
- Utilities
- Analysis
Let’s dive into these Components:
↪ Scanners: Used to rapidly scan remote systems for a single pience of information using remote queries.
- Input: Target (DNS or IP)
- Output: One Line (String or CSV)
- Command:
Invoke-HuntScan.ps1
↪ Surveys: Used to collect from each windows host comprehensive information such as:
- Active Processes
- Loaded Modules/Drivers
- Active Connections
- Accounts
- Key Event Logs
- … etc
↪ Discovery: Discovery functions and cmdlets are used to identify hosts on the network and build a target list that can be ingested by the scanners and survey deployment cmdlets. The following commands can be used: Get-HuntTargets and Invoke-HuntPortScan.
↪ Analysis: This module provide 2 functions:
- Survey Analysis: Comapare survey results against reputation data from local store and VirusTotal. The commands used are for example
Update-HuntObjectandInitialize-HuntReputation. - File Analysis: These functions are a set of utilities to analyze files and malware. The commands used are for example
Get-VTReport,Get-VTStausandGet-Hashes.
↪ Utilities: Utility functions provide the base functionality for deployment and execution of surveys and scans. We can use Invoke-HuntSurvey, Get-HuntSurveyResults and Invoke-HuntScanner.
Installation: PSHunt
Kansa
Kansa is another tool that can be hugely useful for both threat hunting and incident response. It is decribed as “modular incident response framework in Powershell”.
For hunters, one of the biggest challenges they face can be establishing the baseline of “what is normal” in their environment. Kansa can help speed up that task tremendously.
Installation: Kansa
“To beat a hacker, you have to think like a hacker” 💙
![]()



